2024 古剑山 WriteUp By A1natas
附件链接: https://pan.baidu.com/s/1KPm_aNTsFHf7v-nzu-c4cg?pwd=ijpf
Reverse
ipa
IOS 逆向,直接用 ida 打开分析 里面的 EasyIOS
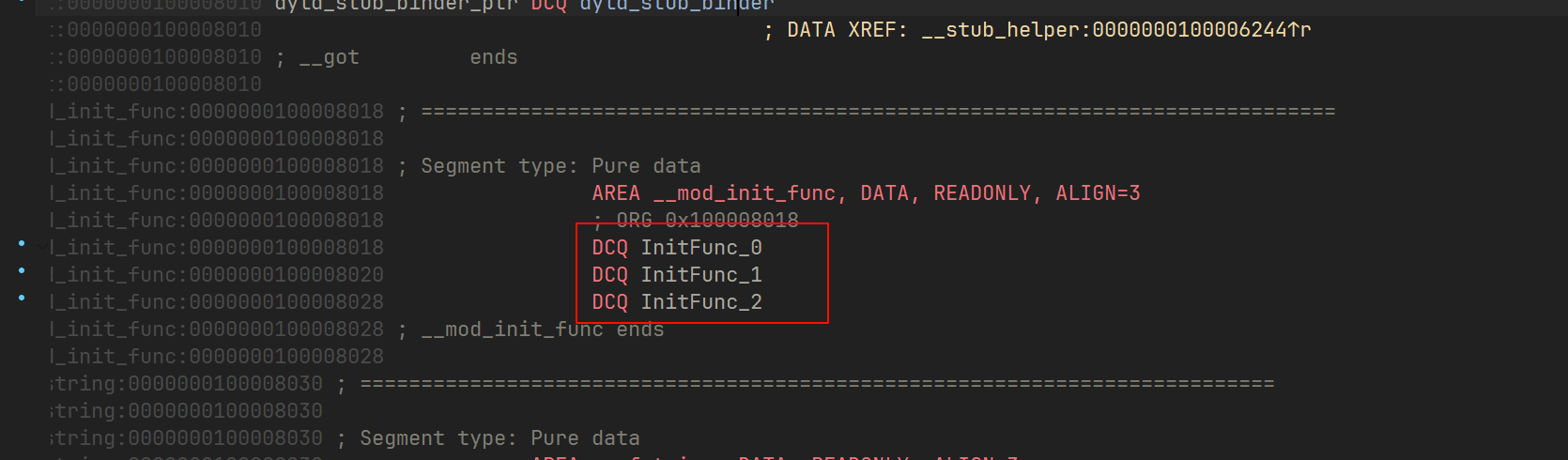
在程序段下有三个初始化程序,里面把 密文、RC4 的 key、还有 base64 的表都给修改了
1 | double InitFunc_0() |
直接运行可以得到码表 NF01ihUKST9q3lnjEBs47k2w5ad+AVHfPezg/CDyxrMLR6GvomIQJOXcpW8ZbutY
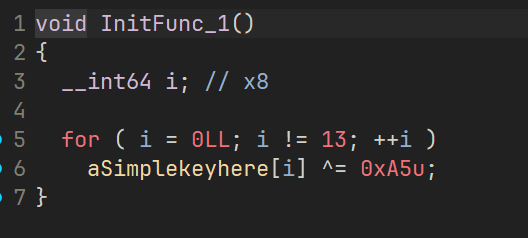
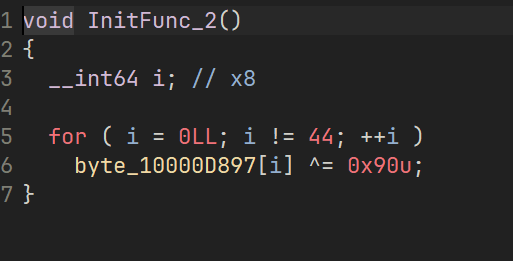
得到 base 后的密文 bExa9y+XlAbleJPlBJy5r0AFPeJQKEODCQ6D23jOpR+X
这里这个 RC4 直接动调出 SBox 然后用剩下的代码直接解就行了
1 | unsigned char data[250] = { |
1 |
|
ez_re
发现有个壳,用 x32dbg 调试,下断点在 VirtualProtect 运行几次然后单步走两下断在程序段
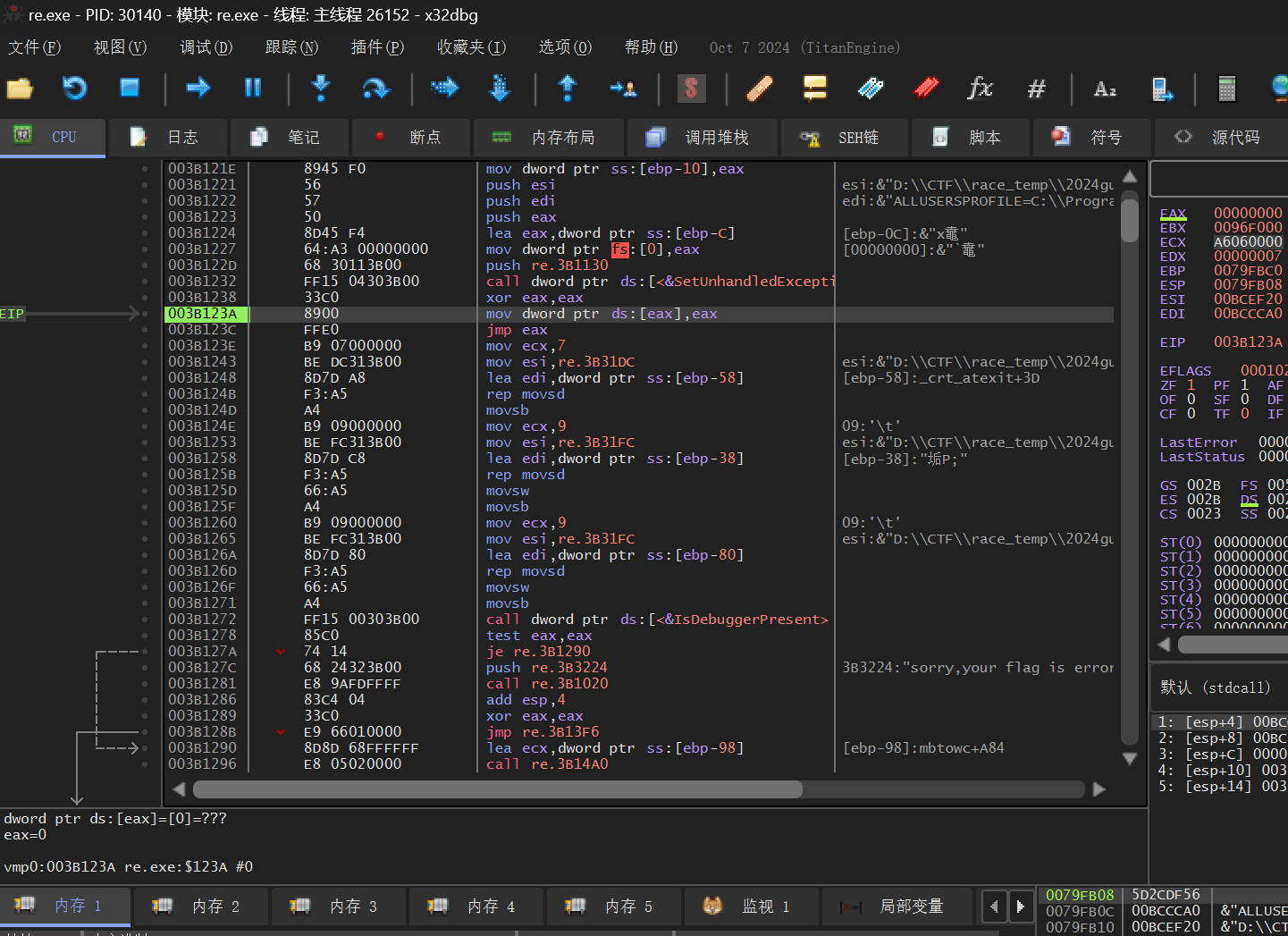
然后用 Scylla dump fix,拉进 ida 分析
手动重命名一下函数后发现,就是一个替换
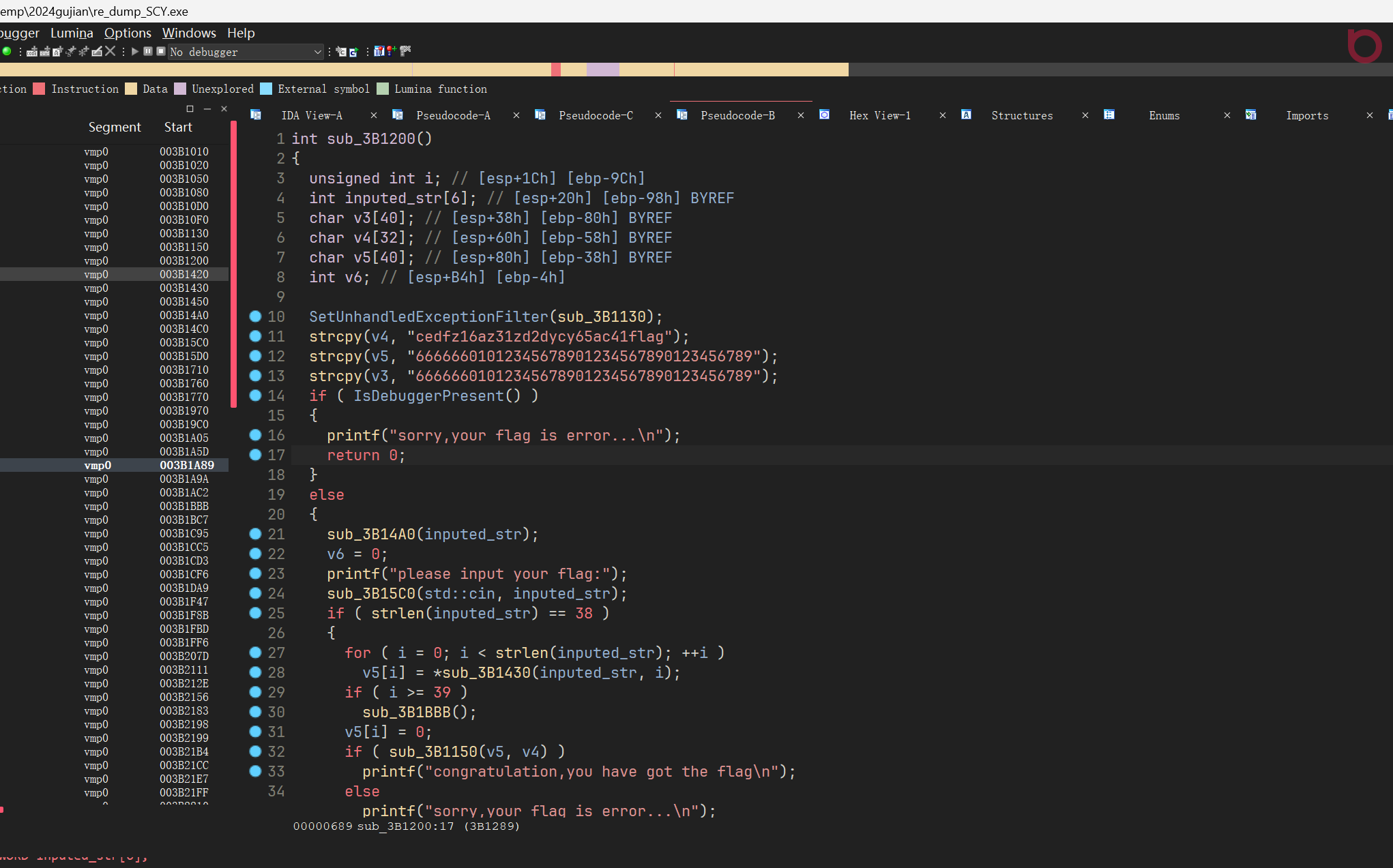
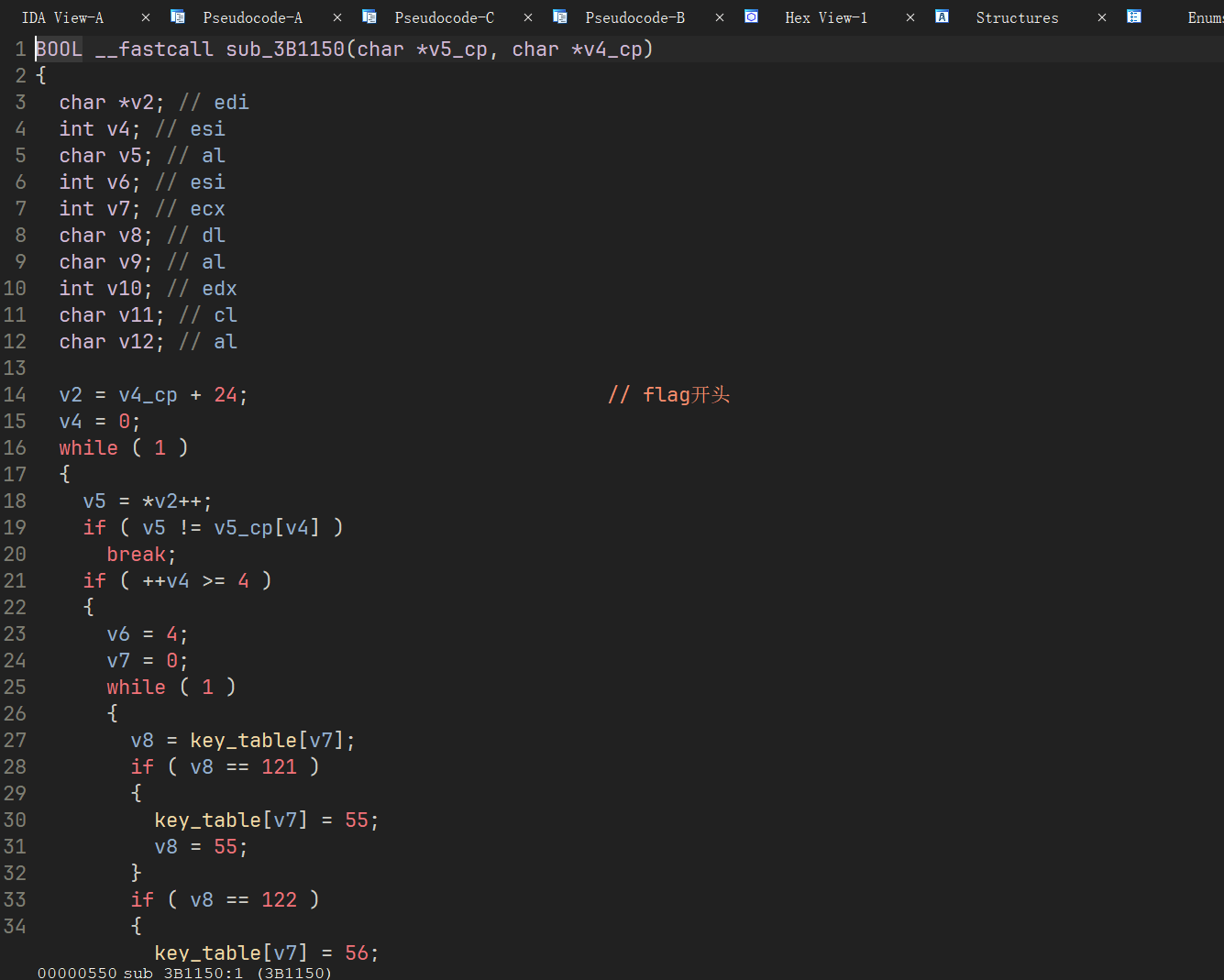
直接把伪C拉下来,改一下判断,加上打印就可以得到 Flag
1 |
|
Misc
蓝书包
拿到一大堆压缩包,随便爆破两个压缩包的密码
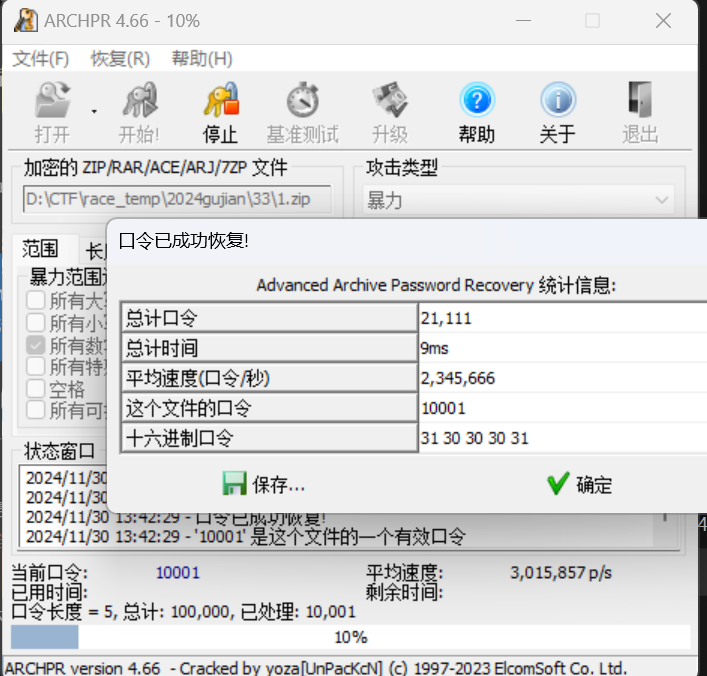
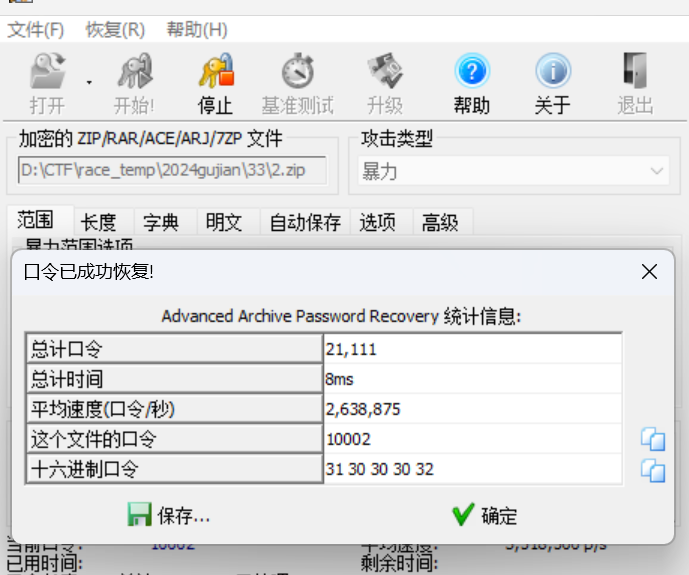
发现密码和文件名有关系,写一个脚本批量解压
1 | import zipfile |
saa 里面有 PNG 文件头,那么把所有解压得到的文件按照字母序拼在一起
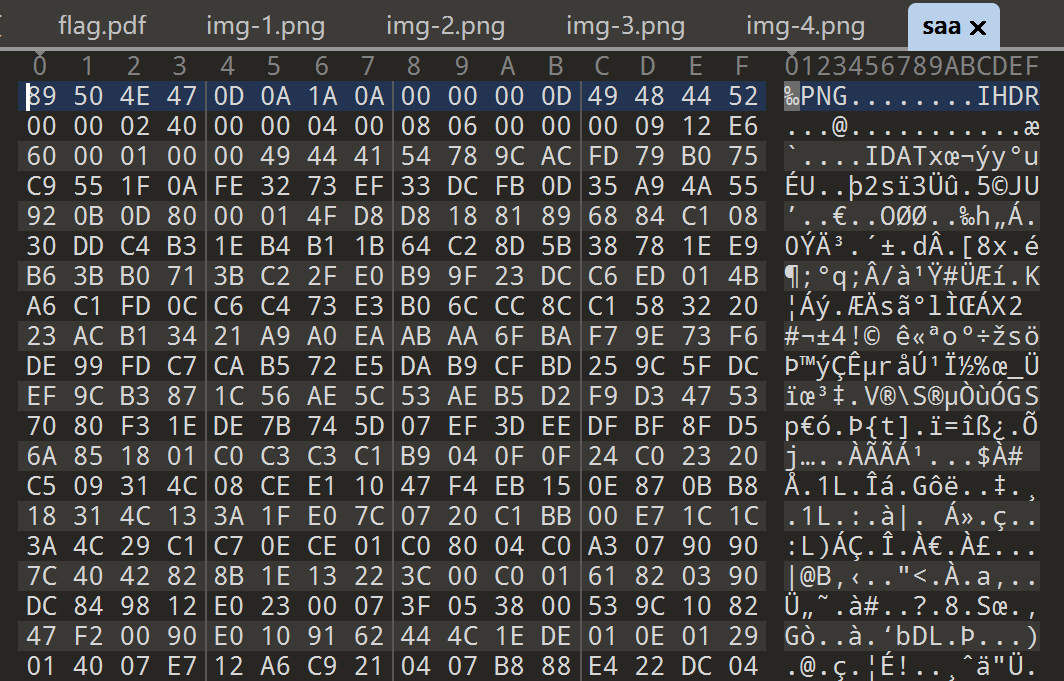

1 | import zipfile |
联想到题目名 蓝书包 那么这张图片应该有 LSB 隐写,StegSolver 没法直接提取出来 应该是加密的 写一个脚本爆破
1 | import threading |
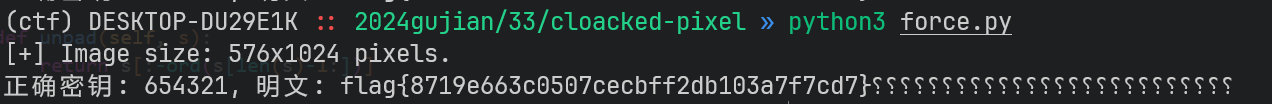
jpg
到手解压得到 att.jpg,大小明显有点不对,binwalk 出一个压缩包,看了一下是伪加密,010 去除后解压得到 flag.pdf
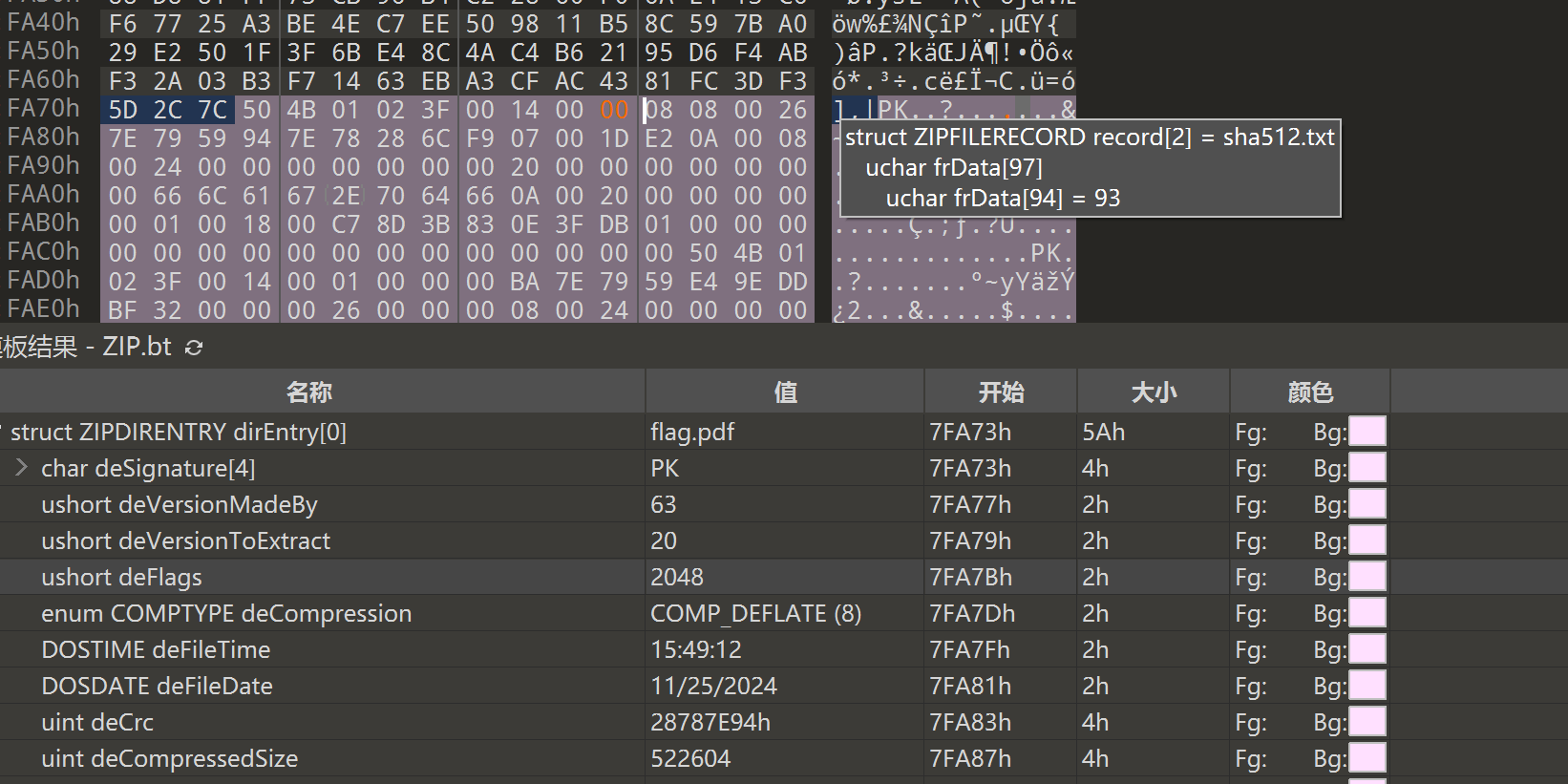
同时压缩包内还有一个 sha512.txt 暂时不知道是什么意思,flag.pdf 试过了许多方法,透明文字啥的都没能解出来
后面尝试用 strings 提取所有可打印字符串,结果在文件末尾发现了大量 Photoshop 字眼,猜测这可能可以通过 ps 打开
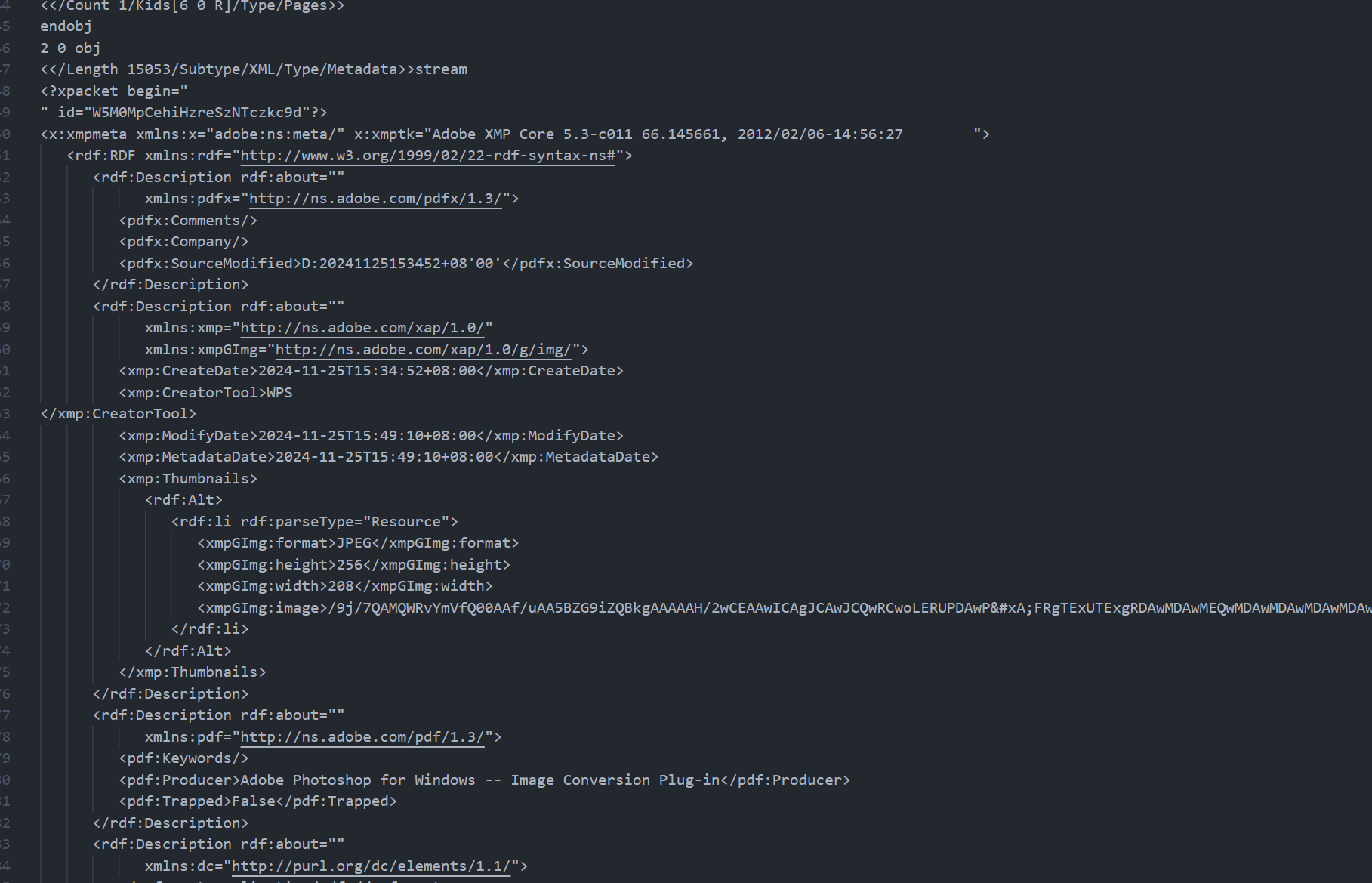
随便保存一份 PSD,然后 Strings 可以发现其中也有这种类似的 XML 结构
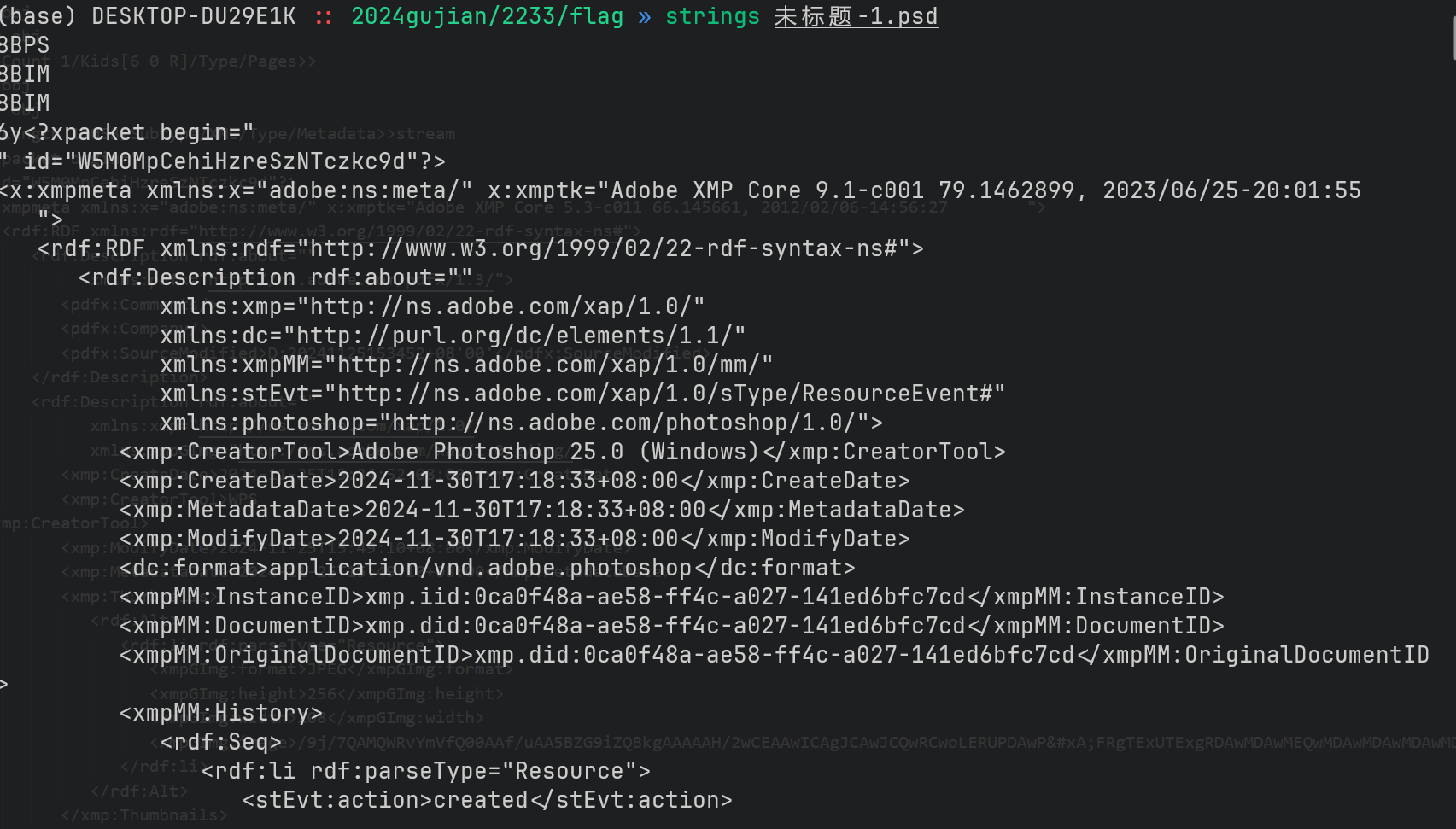
直接用 PS 打开 flag.pdf 文件
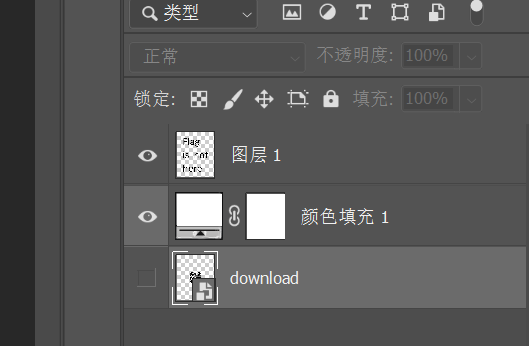
切换到第三个图层,得到一个二维码

解码得到一串 sha512 值,结合前面的 sha512.txt 猜测是明文攻击
1 | 67f480eff11781617044bd47fb9535cfb0e4b6a09e51daff2107c536e9d4eebb3d517cfea6e3f176d4e0d37a9f3658845f3d1917cfce30a4f44ffa2e0af58485 |
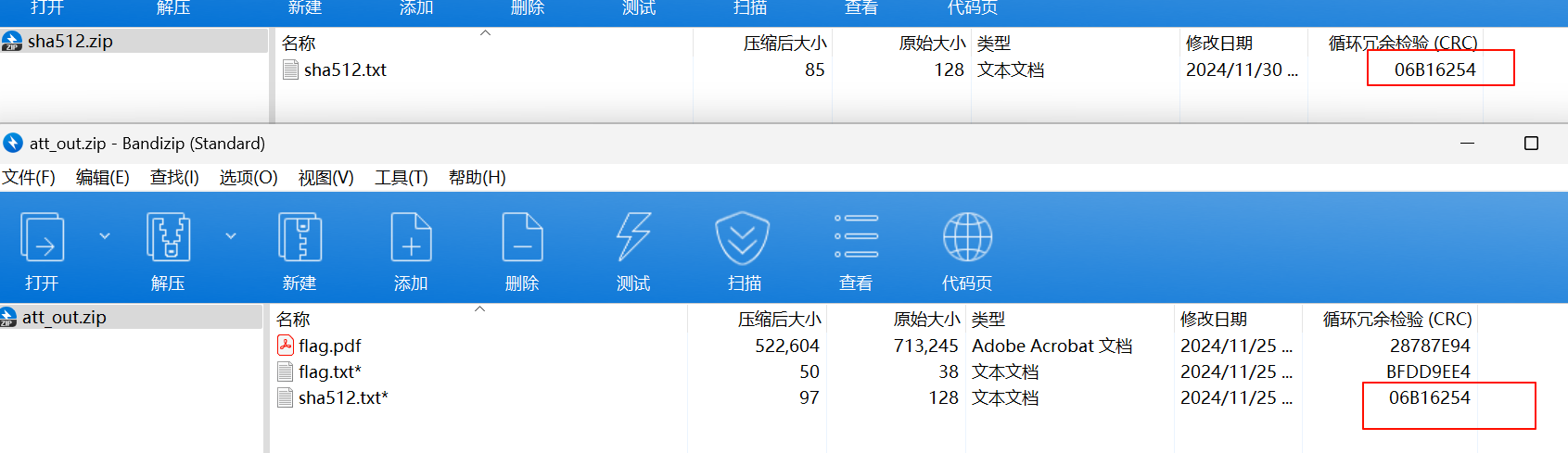
确实是明文攻击,接下来用 ARCHPR 破解就行了
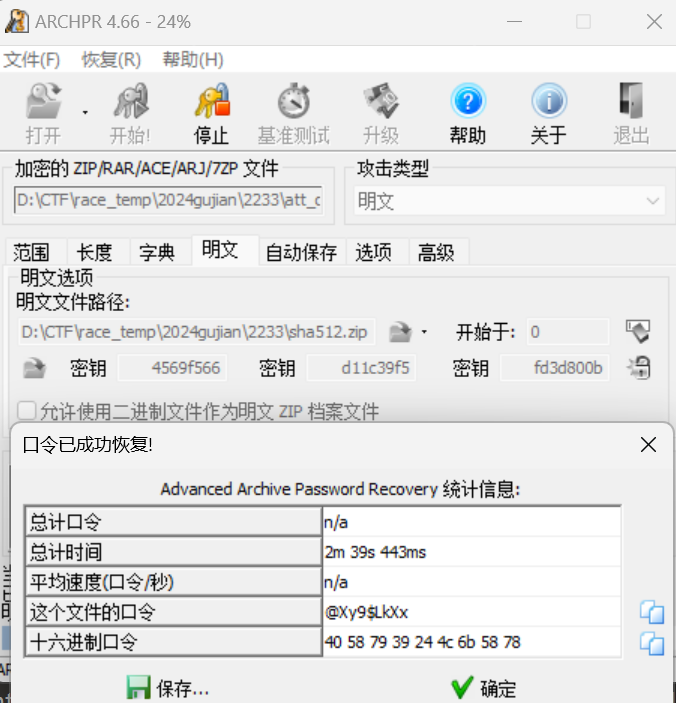
得到压缩包密码 @Xy9$LkXx
flag{10e23151aa0da35221a81dff81a53b4e}
Crypto
cs
可以看到 分离成前一位之后 就能得到一串jjkk的字符串和一串字符
发现hnci对应的flag 字符都是对应ascii码都是减2
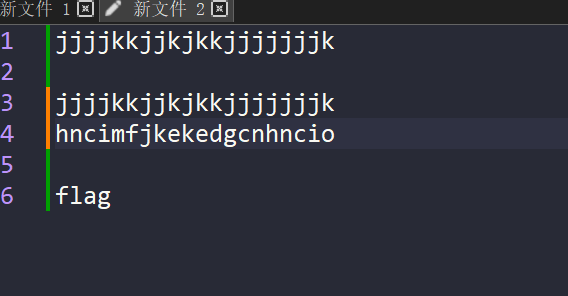
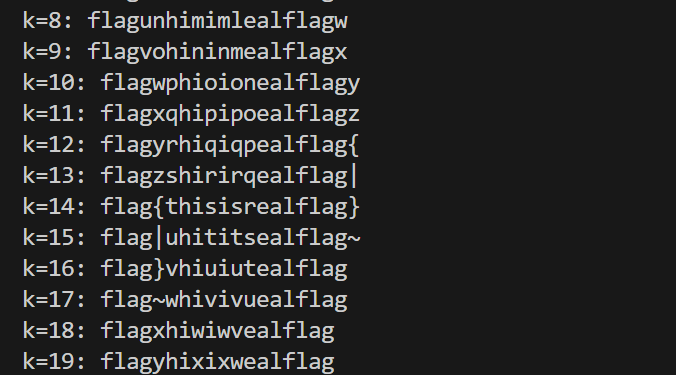
这里只知道f的 不知道k的是什么 写个脚本爆破即可
1 | str1 = "jjjjkkjjkjkkjjjjjjjk" |
PWN
mis
申请的堆块大小由输入的数据长度,而非输入的size,导致存在堆溢出,通过堆溢出达成伪造大chunk放到unsortedbin,泄露libc,然后堆块重叠达成uaf,打__free_hook。
1 | from pwn import * |
in
先申请大chunk,会申请到libc上面,然后利用越界写,通过stdout泄露libc,之后打exit_hook。
1 | from pwn import * |
Web
UN
访问f=index.php 读取源代码
构造反序列化链 这题不需要绕过wakeup也能rce
1 |
|